CyberDefenders - $tealer CTF

Intro
CyberDefenders.org, hosted a fun 24-hr reversing CTF. For those that don’t know about CyberDefenders they host a platform deticated to training BlueTeam skills: Incident response, digital forensics, security analysts, etc). If you are used to VulnHub and Hack-the-box, these services are typically geared more towards redteaming and penetration testing. This is where CyberDefenders stand out!
Nidal Fikri, went to the effort of creating this CTF, and has a more thorough write-up hosted on his own website. So I think he deserves a big thank you, for his effort!
The Objective
Your enterprise network is experiencing a malware infection, and your SOC L1 colleague escalated the case for you to investigate. As an experienced L2/L3 SOC analyst, analyze the malware sample, figure out what it does and extract C2 server and other important IOCs.
P.S.: Make sure to analyze files in an isolated/virtualized environment as some artifacts may be malicious.
Stealer
1) The provided sample is fully unpacked. How many sections does the sample contain?
Hint:
- Use PEStudio or PEBear
Or
import struct
import pefile
import pydasm
pe = pefile.PE('./malware.bin')
print("Number of Sections within PE: " + hex(pe.FILE_HEADER.NumberOfSections)
Answer:
4
2) How many imported windows APIs are being used by the sample?
Hint:
- Use IDA_free, or ghidra or pestudio
- Look at imports section
Sleep OutputDebugStringA
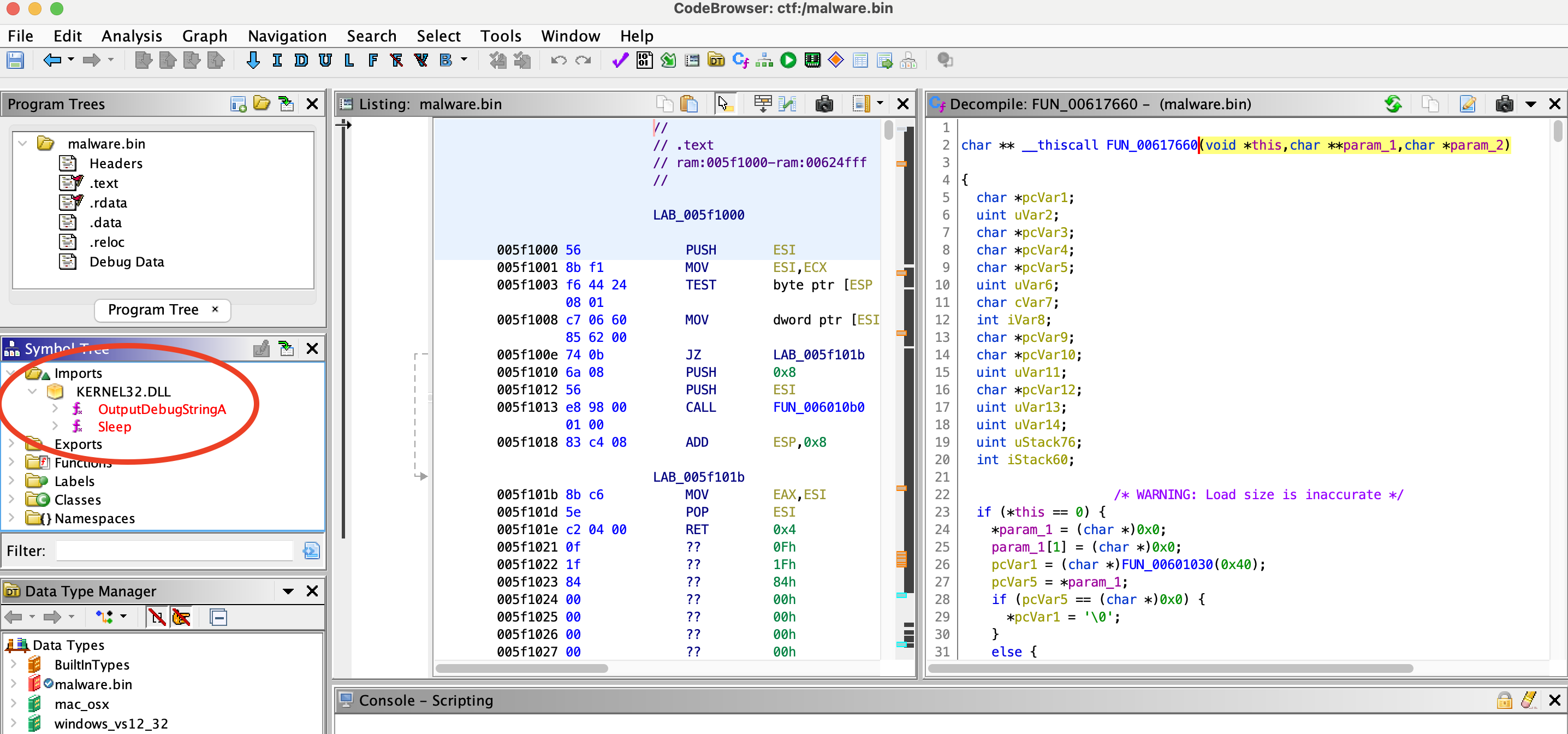
Answer:
2
3) The sample is resolving the needed win APIs at run-time using API hashing. Looking at the DllEntryPoint, which function is responsible for resolving the wanted APIs?
Hint:
- Use IDA_free
- if using Ghidra change FUN_006XXXXXX to sub_6XXXXX
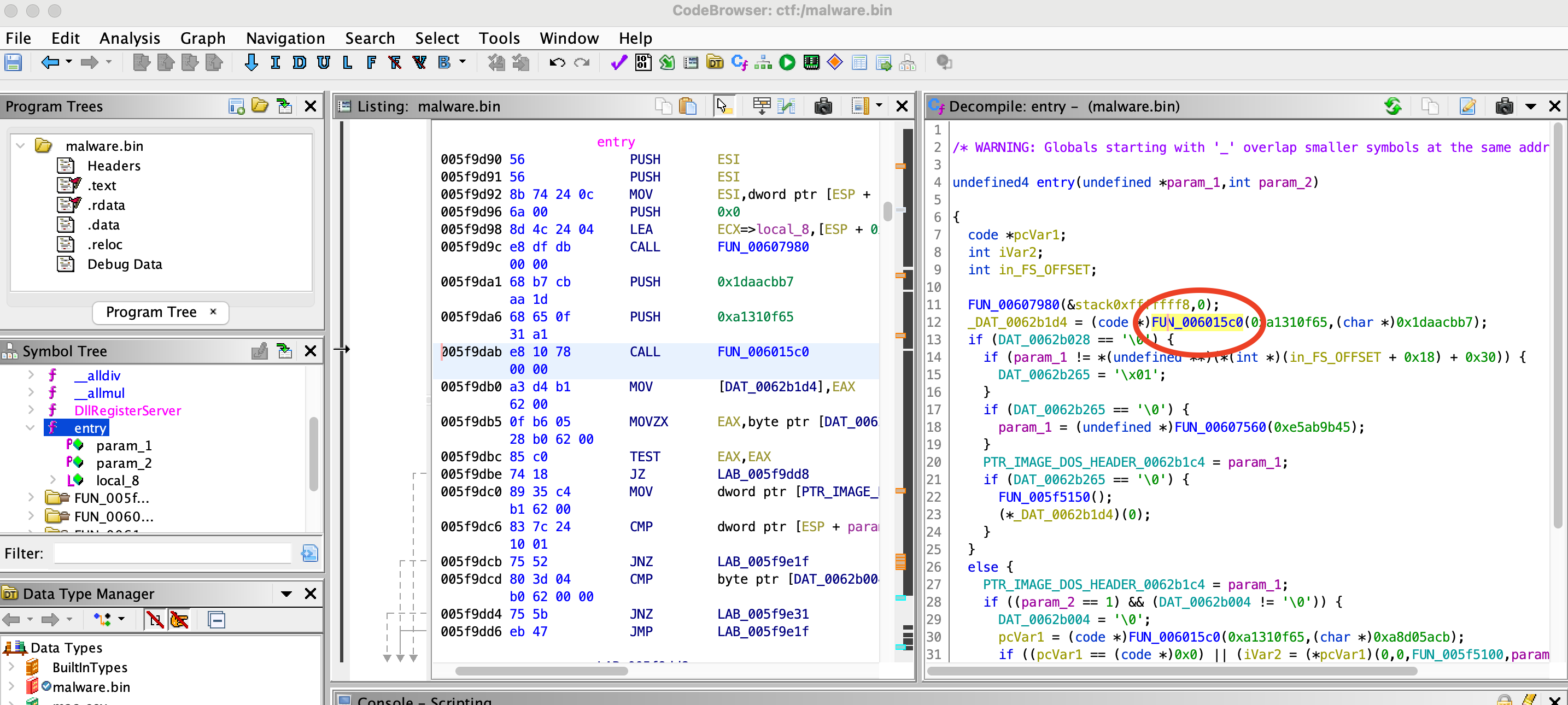
Answer:
sub_6015c0
4) Looking inside the function being described in question 3, which function is responsible for locating & retrieving the targetted module (DLL)?
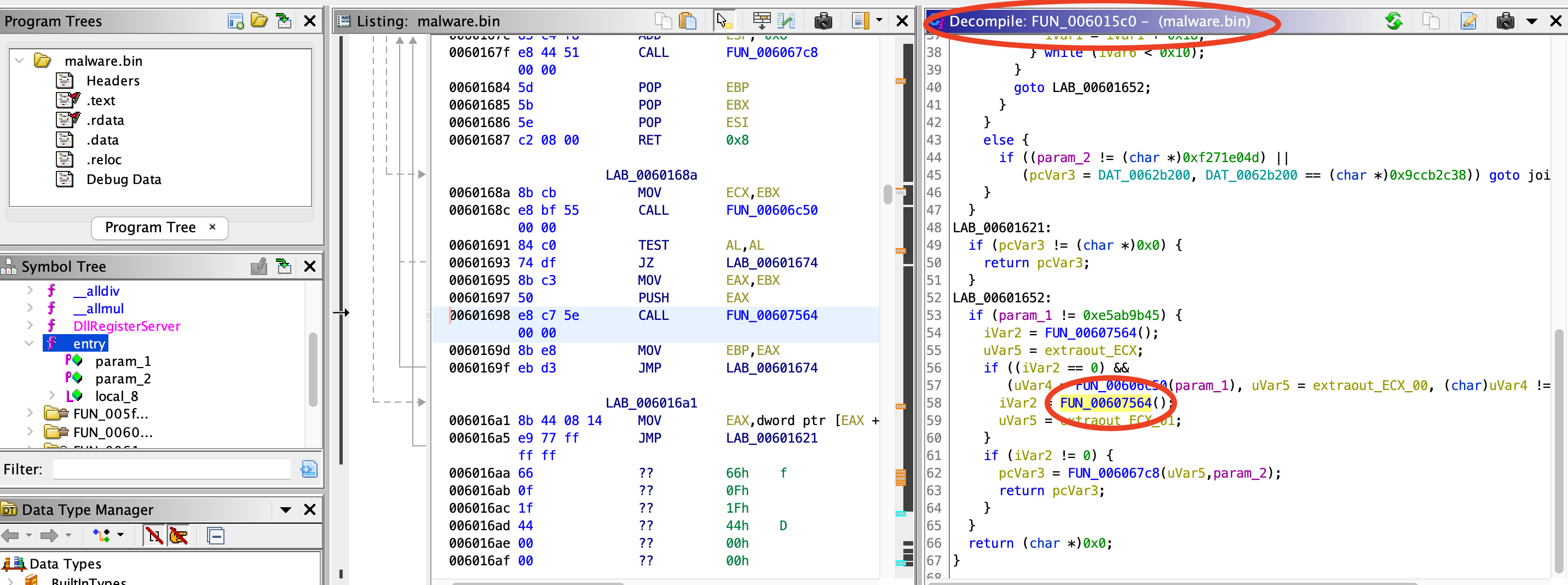
Answer:
sub_607564
5) What type of hashing is being used for the API hashing technique?
Hint:
- Research dridex
- IDA_pro and FindCrypt plugin might work, but we dont have IDA pro?
- Ghidra and FindCrypt-Ghidra - didnt work?
Stepping into function sub_61d620, we can see the polynomial attributed to CRC32:
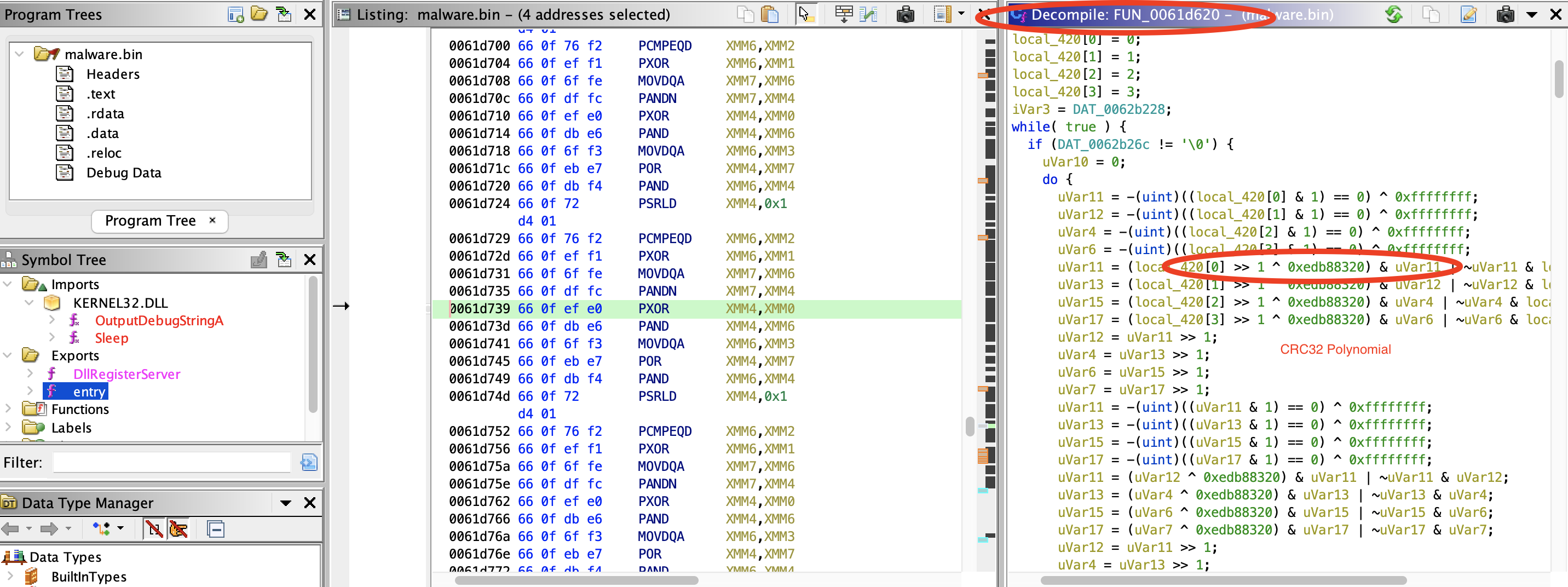
Answer:
CRC32
6) What is the address of the function which performs the hashing?
Hint:
- While tracing various function calls, we stumbled upon this while answering question 5 (see screenshot above)
Answer:
0x61d620
7) What key is being used for XORing the hashed names?
Hint:
- follow _entry
- sub_6015c0 or sub 6067c8
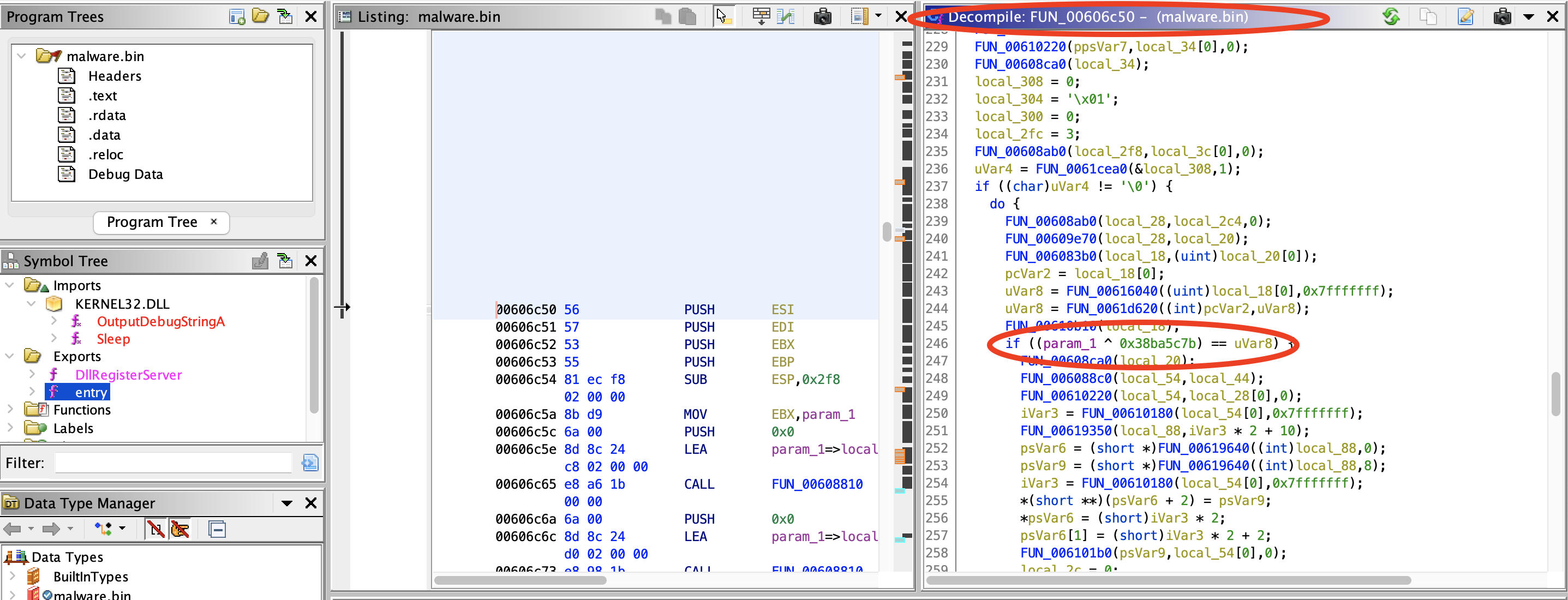
Answer:
0x38ba5c7b
8) What information is being accessed at the address 0x60769A?
Hint:
- We’re past the dynamic dll imports and export table
- PEB
- Not Ldr but what address do we need to know before we can start calling API’s
Answer:
BaseAddress
9) Looking inside the function being described in question 3, which function is responsible for locating & retrieving the targetted API from the module export table?
Hint:
- go back to the answer from question 7
Answer:
sub_6067c8
10) Diving inside the function being described in question 9, what is being accessed at offset 0X3C within the first passed parameter?
Hint:
- Use of Structs
- DOS_IMAGE_HEADER
- File address of new exe header
This was tough, but using the address from Question 11, gave us a hint
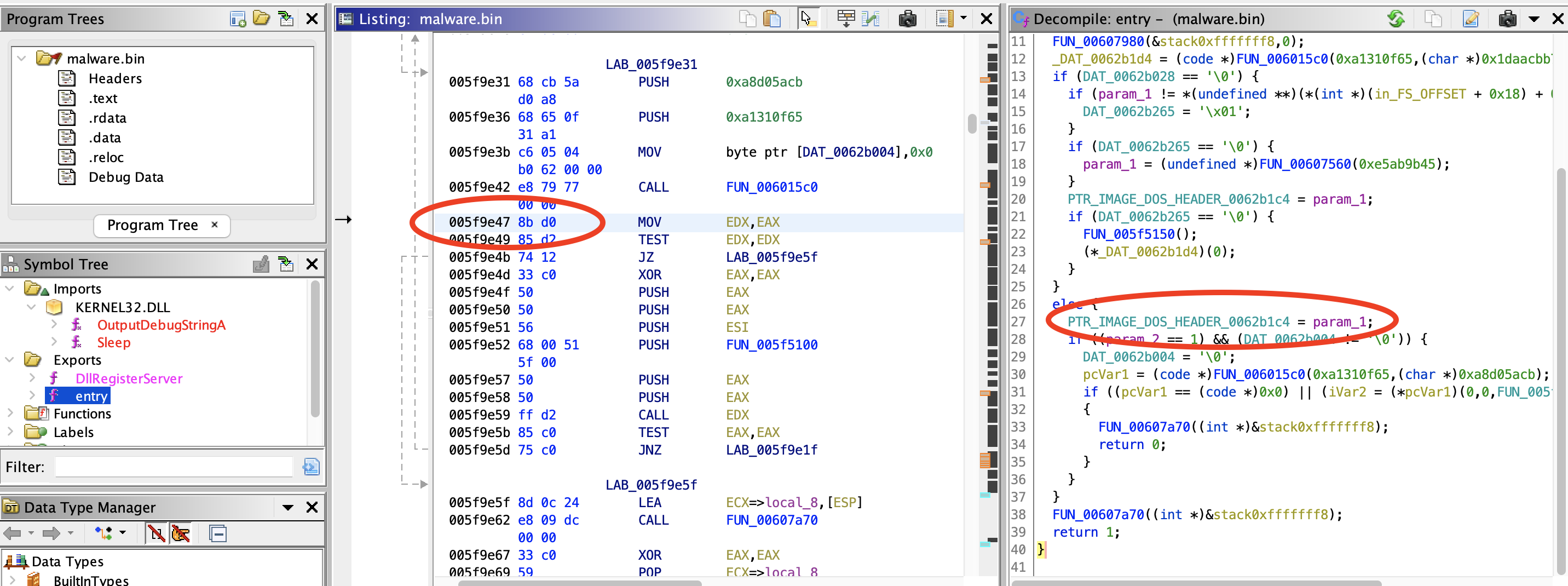
Answer:
e_lfanew
11) Which windows API is being resolved at the address 0x5F9E47?
Hint:
- googled more on dridex and apis
- guessed at virtualalloc -nope
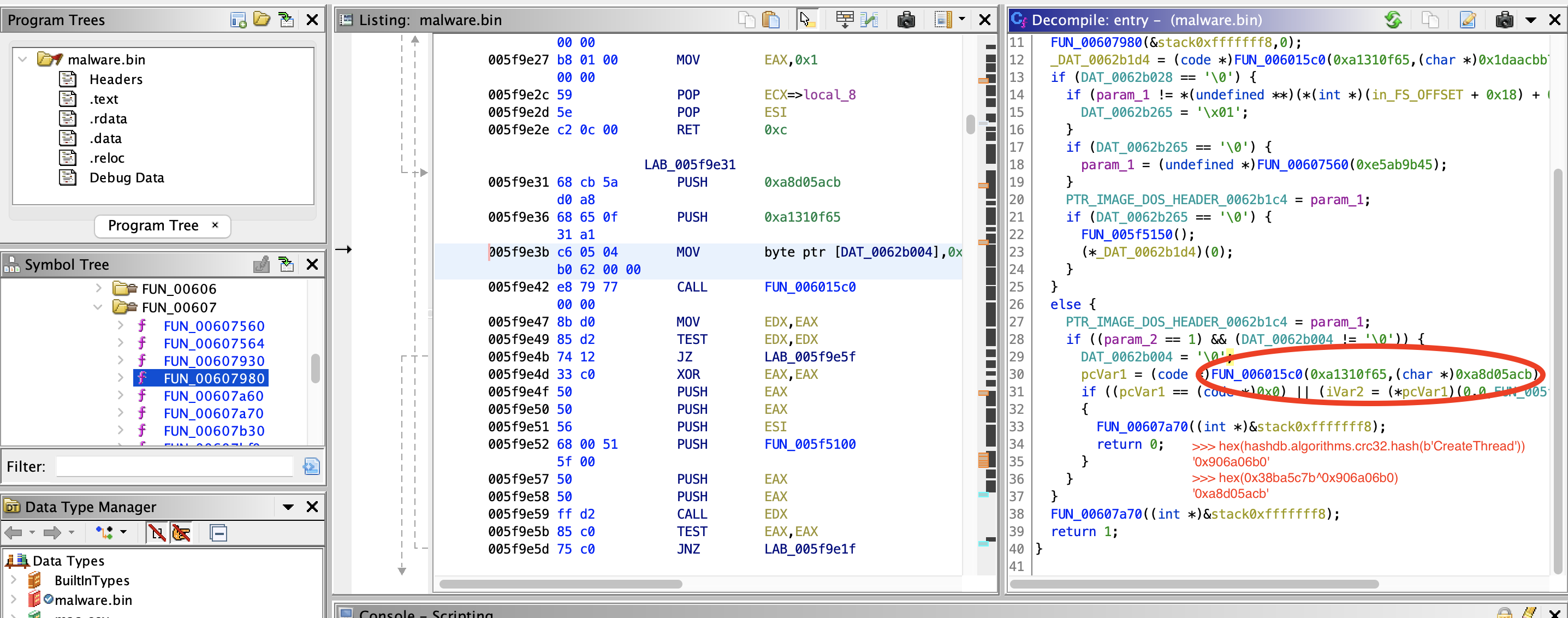
Answer (another guess):
CreateThread
12) Looking inside sub_607980, which DLL is being resolved?
Some more enumeration/guess work, looking for a match to 0x588ab3ea
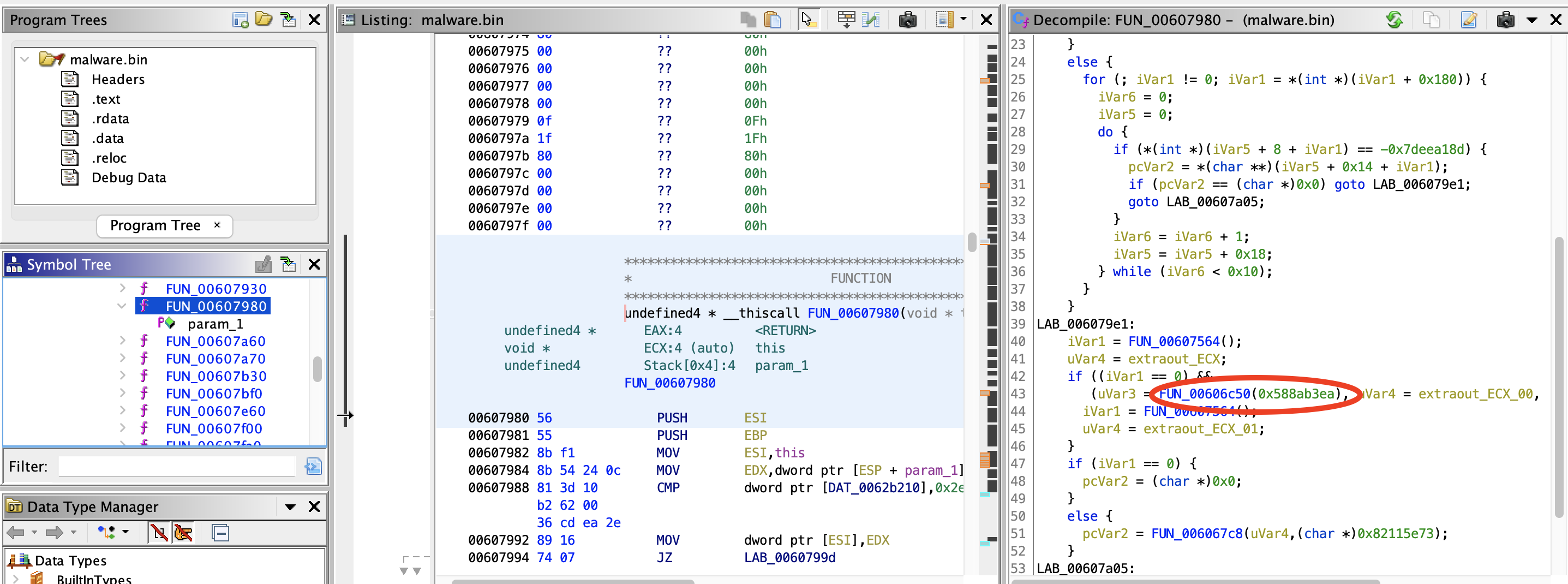
>>> hex(hashdb.algorithms.crc32.hash(b'NTDLL.DLL'))
'0x6030ef91'
>>> hex(0x38ba5c7b^0x6030ef91)
'0x588ab3ea'
Answer:
ntdll.dll
13) Also Looking inside sub_607980, which API is being resolved?
Hint:
- We recommend reading this: blog.lexfo.fr
Answer:
RtlAddVectoredExceptionHandler
14) What is the appropriate data type of the only argument at function sub_607D40?
Hint:
- access violation 0xc0000005
- stack overflow 0xc00000fd
- veh
- exceptions
Answer:
_EXCEPTION_POINTERS
15) After reverse-engineering sub_607980 and knowing its purpose, Which assembly instruction is being abused for further anti-analysis complication, especially when running the sample? (one space included)
Hint:
- This one threw me as i don’t use a space for int3 and was trying int3 retn
Answer:
int 3
16) After reverse-engineering sub_607980 and knowing its purpose, Which assembly instruction is being used for altering the process execution flow? (Also adds anti-disassembly complication)
Hint:
- If last questions answer was int3, this is either retn or ret
Answer:
ret
17) There are important encrypted strings in the .rdata section. Which encryption algorithm is being used for decryption?
Hint:
- Googled: “malware research dridex”
- RC4, 40-byte key
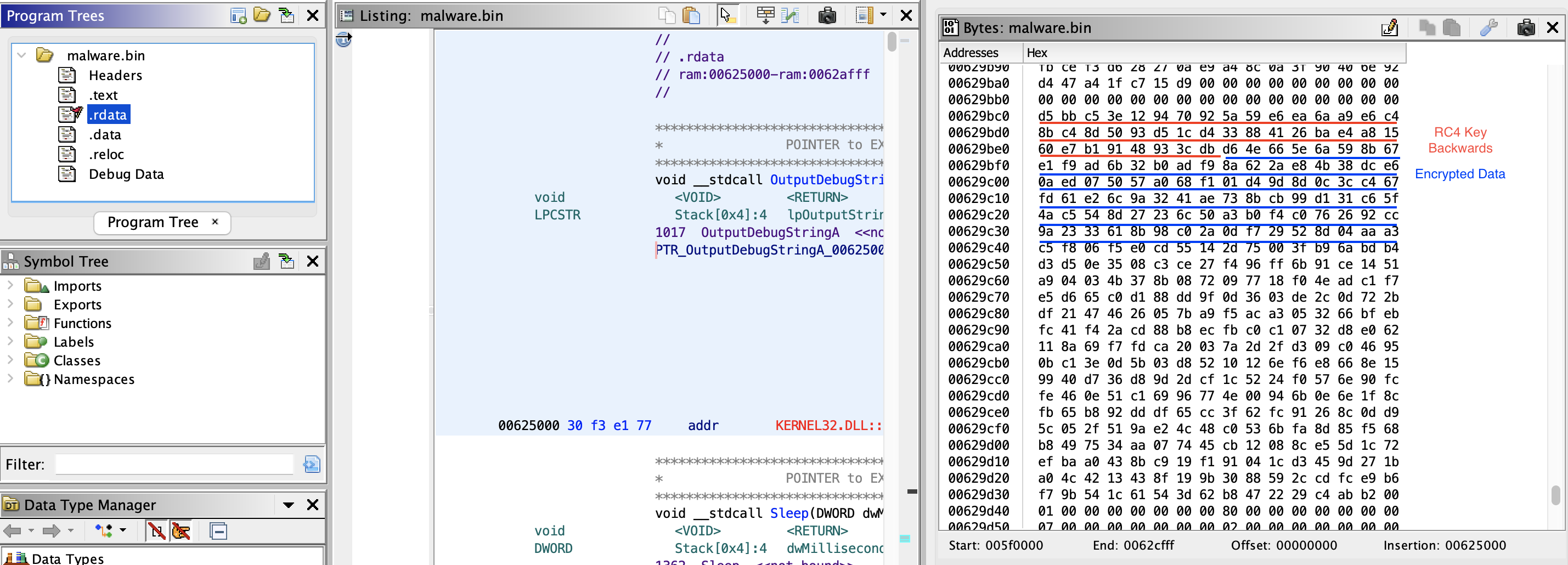
Answer:
RC4
18) What is the address of the function that is responsible for strings decryption?
Hint:
- Is it possible that IDA_pro and findcrypt would have made this easier?
- Ghidra and its FindCrypt plugin sadly didnt work?
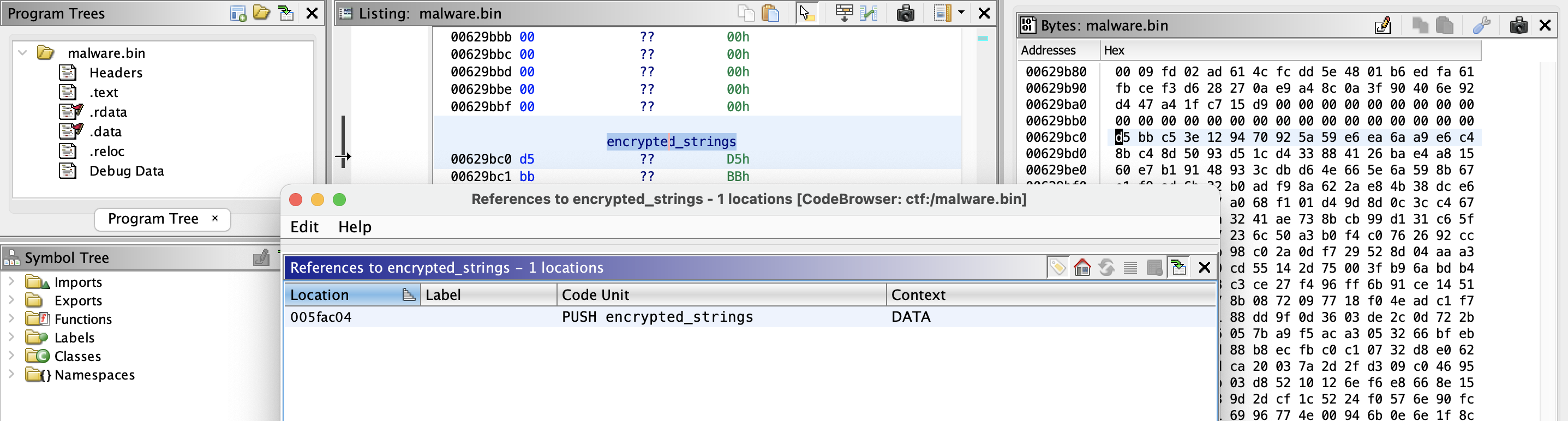
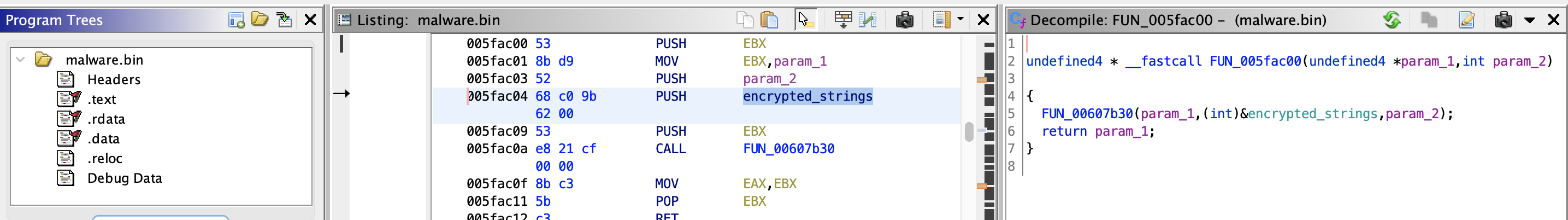
Answer:
0x61e5d0
19) What are the two first decrypted words (space separated strings) at 0X629BE8?
Hint:
- Key and config is encrypted in .rdata (See screenshot above)
- extract the key, reverse it, then RC4 decrypt the blob
- Cyberchef
Program Manager.Progman.AdvApi32~PsApi~shlwapi~shell32~WinInet \ ./run /tn "%ws"."%ws" /grant:r"%ws":F.\NTUSER.DAT.winsxs.x86_*. \ amd64_*.*.exe.\Sessions\%d\BaseNamedObjects\..
Answer:
Program Manager
20) What is the key used for decrypting the strings in question 19?
Hint:
- using the answer from Question 19 as a hint, grab the 40 bytes before that address
- Address: 0x629BC0
Answer (non reversed key):
d5bbc53e129470925a59e6ea6aa9e6c48bc48d5093d51cd433884126bae4a81560e7b19148933cdb
Practise key:
d5 bb c5 3e 12 94 70 92 5a 59 e6 ea 6a a9 e6 c4 8b c4 8d 50 93 d5 1c d4 33 88 41 26 ba e4 a8 15 60 e7 b1 91 48 93 3c db
21) What is the length (in bytes) of the used key in question 19?
Hint:
- Google the size of dridex rc4 key
- Also we already have it from previous question
Answer:
40
22) What is the address of the function that is responsible for connecting to the C&C?
Hint:
- This was a pain, bouncing around in ghidra, tracing functions
Answer:
0x623370
23) What is the first C&C IP address in the embedded configuration?
Hint:
- We recommend reading this: blog
- This tool can also do it (-v flag) Github Appgate Dridex
## Botnet ID:
10444
## C2 Addresses
192.46.210.220:443
143.244.140.214:808
45.77.0.96:6891
185.56.219.47:8116
Answer:
192.46.210.220
24) What is the port associated with the first C&C IP address?
Answer:
443
25) How many C&C IP addresses are in the sample configuration?
Answer:
4
26) What is the address of the function which may download additional modules to extend the malware functionality?
Hint:
- sub_623370
- sub_623820
- sub_623820
- InternetReadFile API
Answer:
0x623820
References
Share on: