Bsides London 2021 CTF - Denominate
Denominate CTF
Below is our walkthrough to the Bsides 2020/21 London CTF Denominate, created by Hack-The-Box (HTB)
Rated as medium difficulty.
CTF Brief
Our client’s network has been compromised, so we captured some traffic for analysis, can you find out what attacker did inside his network?
The file capture is available to download here
CTF Walkthrough
When we first open the packet, there is a lot of UDP packets, initial eyeball inspection indicates RTP. So we right click choose to follow a stream, then right-click again, choose “decode as…”, in the new window we use the pulldown menu on the Current column to and select RTP!
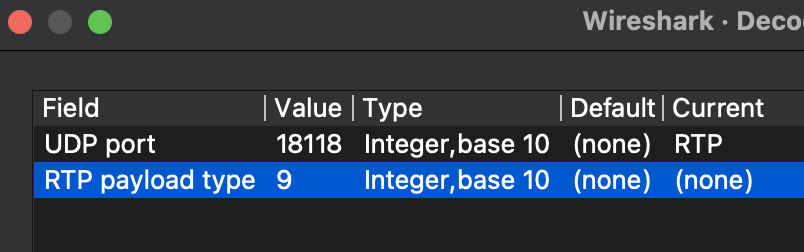
All RTP packets should now be correctly decoded:
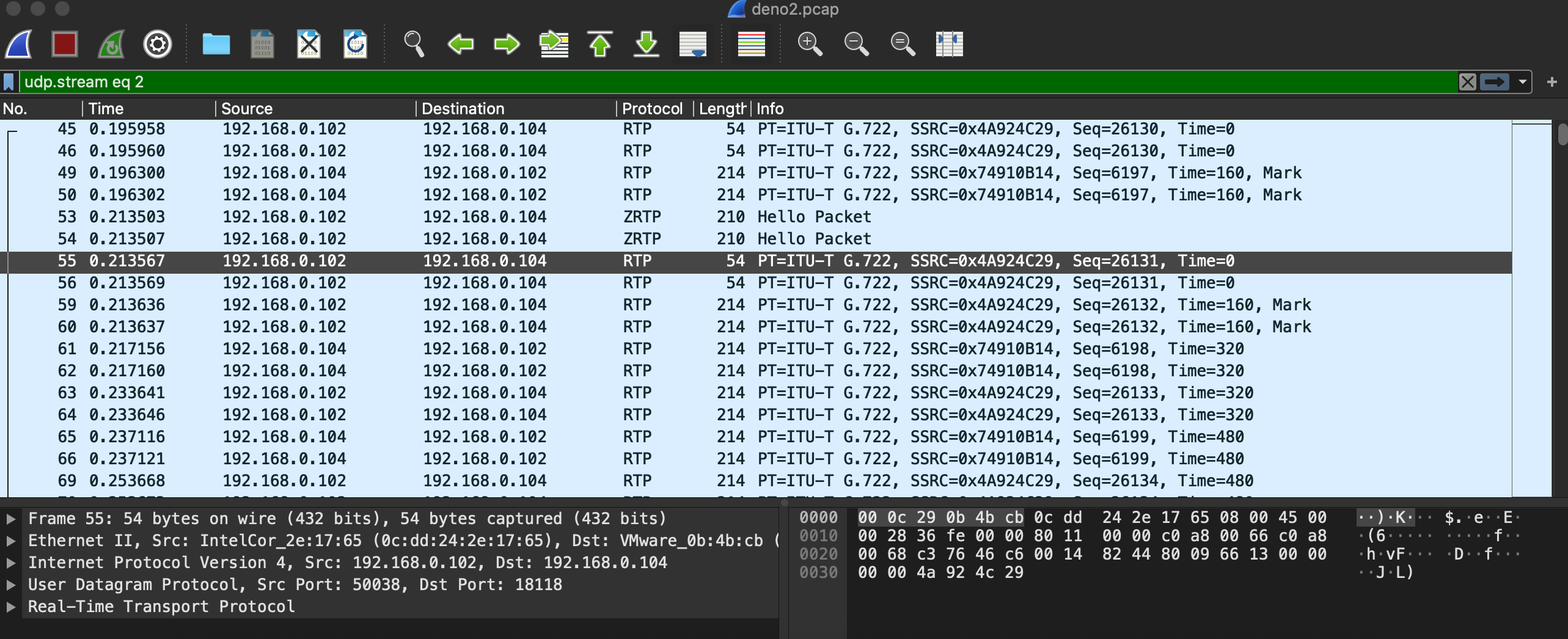
Next we want to start extracting the audio. We do this through using Wireshark’s built-in telephony modules. Using the menu Telephony - RTP - Streams Analysis
You should then get the below screen, and you can play the RTP Streams:
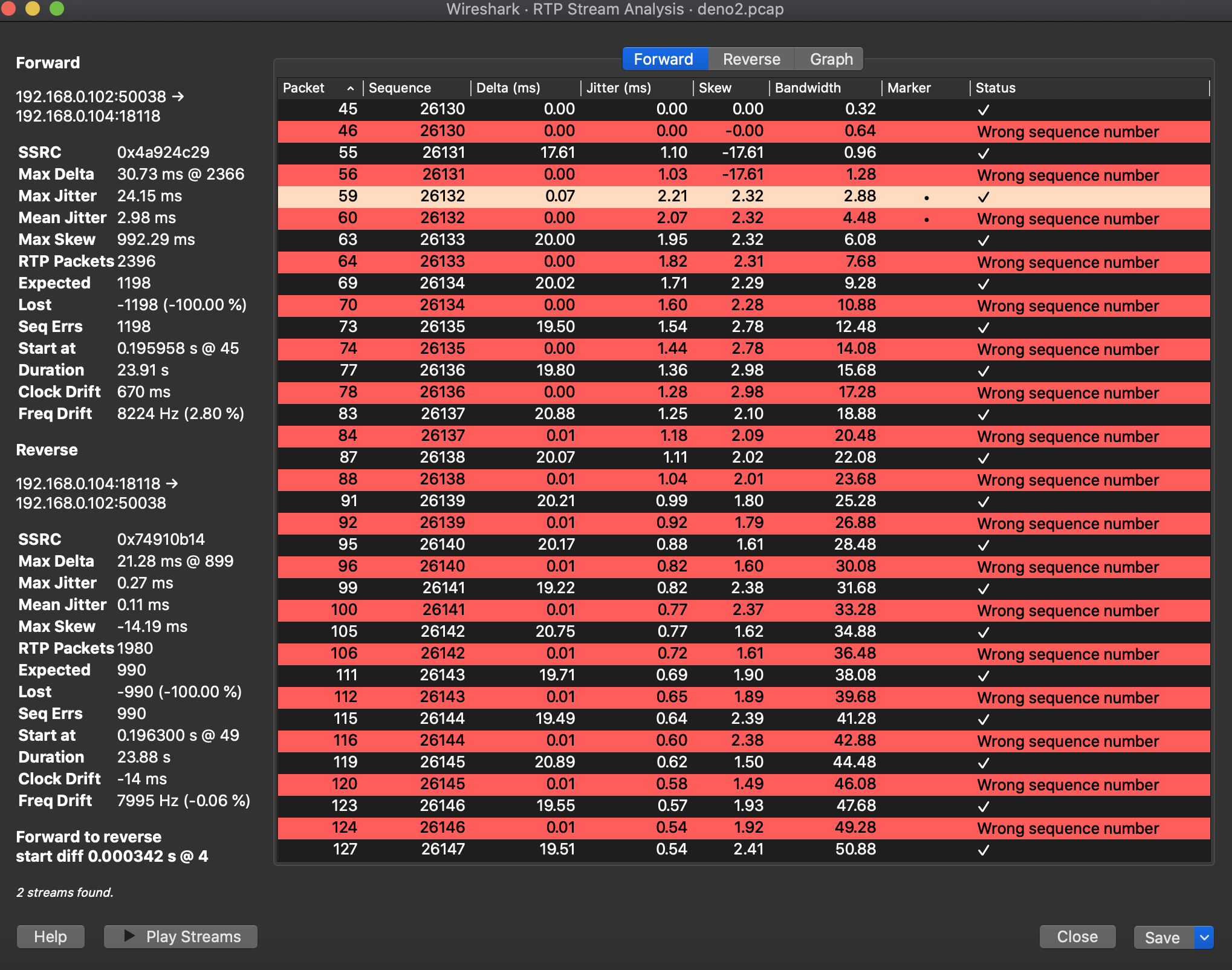
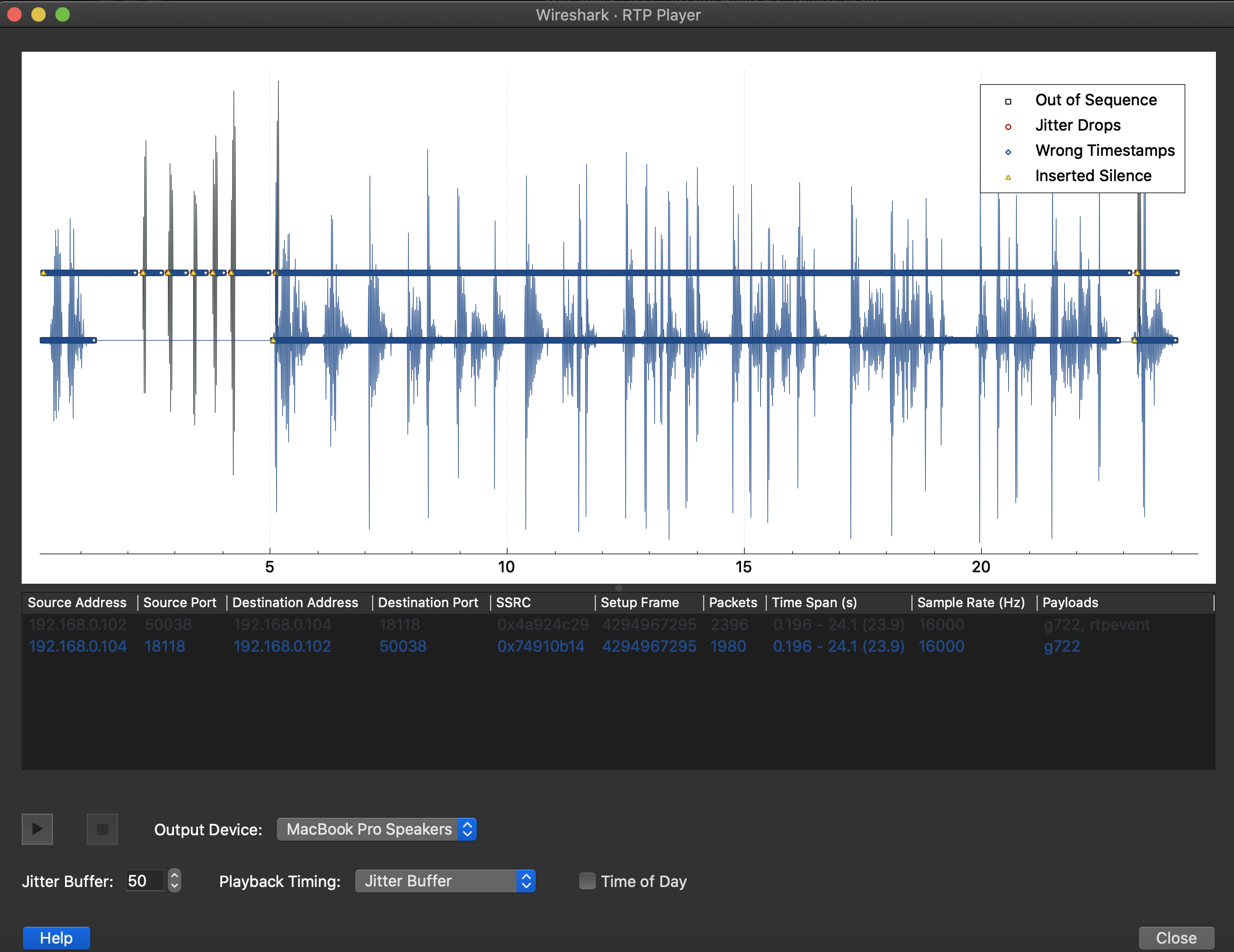
Next we can use Wireshark’s RTP player to play the streams. There appears to be two streams
- Some DMTF tones
- Some noise
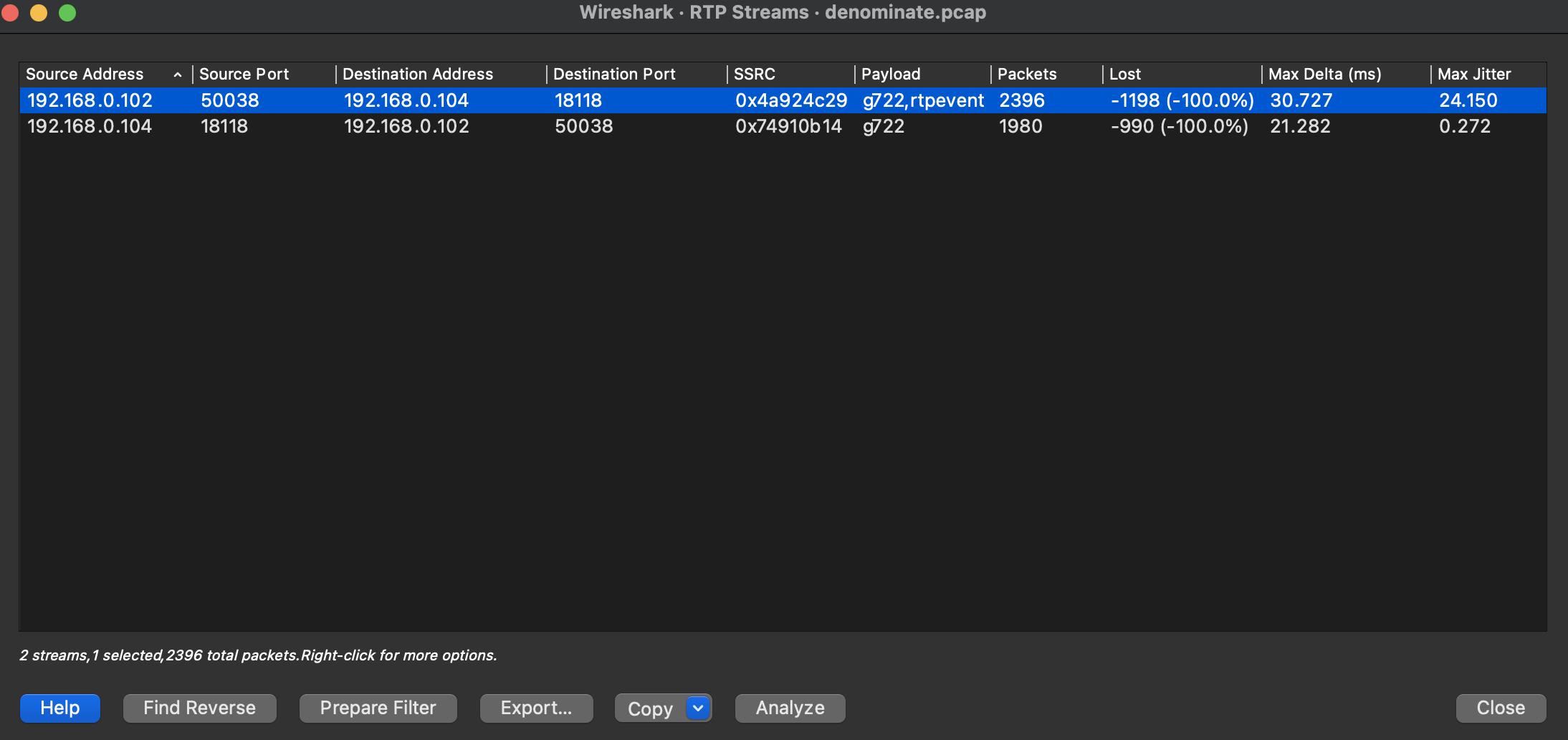
Back to the telephony menu, if this time we choose RTP - RTP Streams, we get a new window, where we can individually select one of the Streams, making playback of the DTMF tomes much cleaner. Click “Analyse” to get to the RTP player.
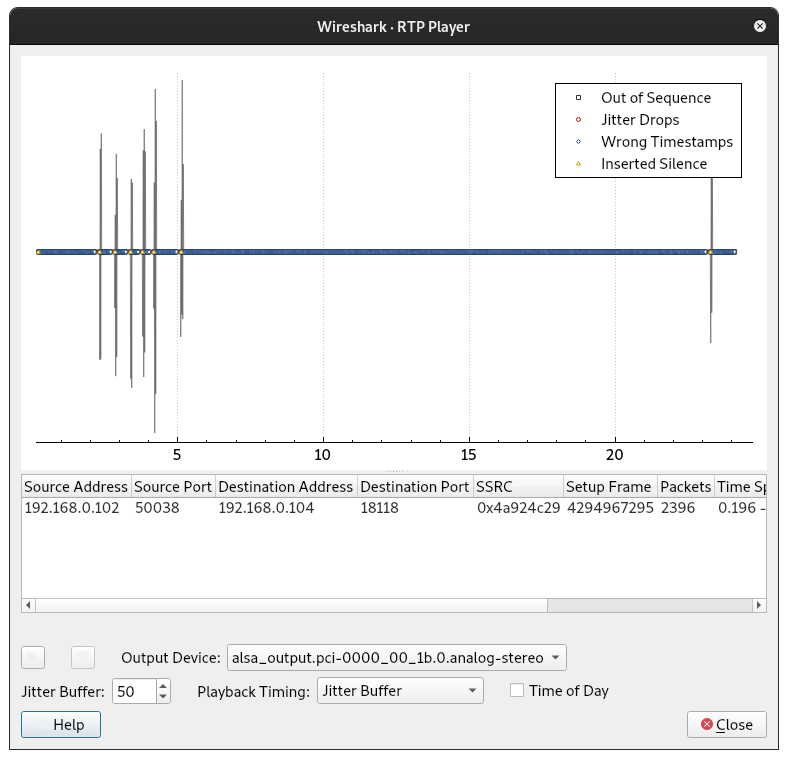
We focus on the DTMF tone stream to see a series of 6 tones.
Using a DTMF decoder on an Android handset, we can decode the tones, as we hold the handset upto the computers speakers.
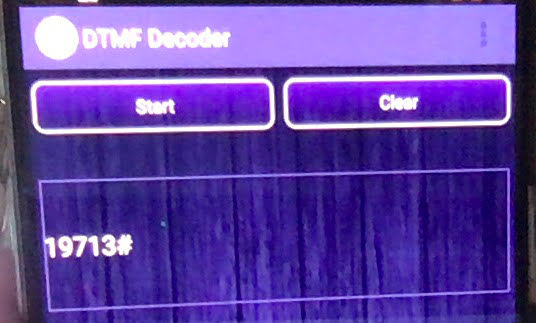
The flag:
HTB{13713#}
Share on: