Windows Defender & Silent Rules

Anti-Virus/Anti-Malware Silent Rules
Sometimes SOC analysts forget about the confidentiallity threat from Anti-Virus(AV) and Anti-Malware(AM) solutions. Having had many painful converstations with 3rd party security providers and online AV scanners when SOAR platfroms have automatically uploaded confidential documents without manual user confirmation. You can find yourself having to negociate the deletion of files that contain business sensitive information or personal identifying information.
Florian Roth recently highlight this point in these tweets:
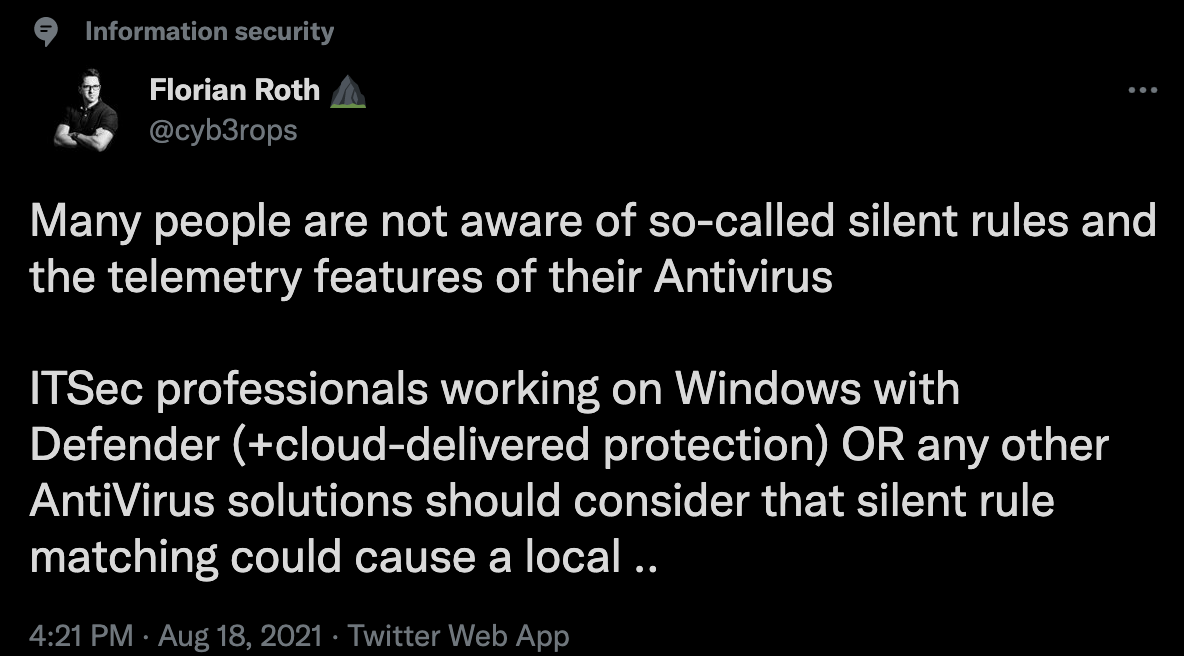
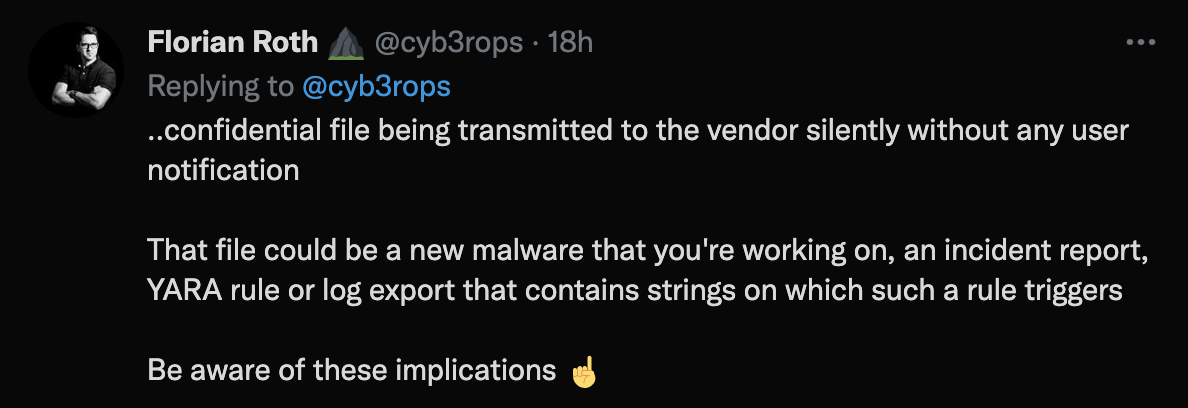
Florian Roth then tweeted about the following PDF from Germany’s BSI group about disabling Microsofts Telemetrics BSI Analyse_Telemetriekomponente_1_2.pdf
This post will cover the english translation on disabling the telemetrics outlined in the above document.
DNS blocking via /etc/hosts
The telemetry hostname list is as follows:
| Hostname | Location |
| geo.settings-win.data.microsoft.com.akadns.net, db5-eap.settings-win.data.microsoft.com.akadns.net, settings-win.data.microsoft.com, db5.settings-win.data.microsoft.com.akadns.net, asimov-win.settings.data.microsoft.com.akadns.net | Ireland (IRL), Dublin |
| db5.vortex.data.microsoft.com.akadns.net, v10-win.vortex.data.microsoft.com.akadns.net, geo.vortex.data.microsoft.com.akadns.net, v10.vortex-win.data.microsoft.com | Ireland (IRL), Dublin |
| v10.events.data.microsoft.com, v20.events.data.microsoft.com | Virginia (US), Washington |
| us.vortex-win.data.microsoft.com | Virginia (US), Boyton |
| eu.vortex-win.data.microsoft.com | Netherlands (NL), Amsterdam |
| vortex-win-sandbox.data.microsoft.com | California (US), Los Angeles |
| alpha.telemetry.microsoft.com | California (US), Los Angeles |
| oca.telemetry.microsoft.com | Wyoming (US), Cheyenne |
| ceuswatcab01.blob.core.windows.net ceuswatcab02.blob.core.windows.net | Iowa (US), Des Moines |
| eaus2watcab01.blob.core.windows.net eaus2watcab02.blob.core.windows.net | Virginia (US), Boydton |
| weus2watcab01.blob.core.windows.net weus2watcab02.blob.core.windows.net | Washington (US), Redmond |
As 0.0.0.0 is a non-routable address we can simply alter the /etc/hosts file (%windir%\system32\drivers\etc\ hosts)
0.0.0.0 geo.settings-win.data.microsoft.com.akadns.net
0.0.0.0 db5-eap.settings-win.data.microsoft.com.akadns.net
0.0.0.0 settings-win.data.microsoft.com
0.0.0.0 db5.settings-win.data.microsoft.com.akadns.net
0.0.0.0 asimov-win.settings.data.microsoft.com.akadns.net
0.0.0.0 db5.vortex.data.microsoft.com.akadns.net
0.0.0.0 v10-win.vortex.data.microsoft.com.akadns.net
0.0.0.0 geo.vortex.data.microsoft.com.akadns.net
0.0.0.0 v10.vortex-win.data.microsoft.com
0.0.0.0 v10.events.data.microsoft.com
0.0.0.0 v20.events.data.microsoft.com
0.0.0.0 us.vortex-win.data.microsoft.com
0.0.0.0 eu.vortex-win.data.microsoft.com
0.0.0.0 vortex-win-sandbox.data.microsoft.com
0.0.0.0 alpha.telemetry.microsoft.com
0.0.0.0 oca.telemetry.microsoft.com
0.0.0.0 ceuswatcab01.blob.core.windows.net
0.0.0.0 ceuswatcab02.blob.core.windows.net
0.0.0.0 eaus2watcab01.blob.core.windows.net
0.0.0.0 eaus2watcab02.blob.core.windows.net
0.0.0.0 weus2watcab01.blob.core.windows.net
0.0.0.0 weus2watcab02.blob.core.windows.net
This addition to the /etc/hosts file can easily be deployed through an organisation via “Group Policy” or a Orchestration platfrom such as Ansible or Puppet.
HTTP Proxies Blocking
Another method of blocking Windows telemetry, this by adding rules to your HTTP proxy. At Netscylla we are fans of Squid proxy, so here are the translated Squid instructions.
Example with squid proxy
Insert the data below into the file: /etc/squid/telemetry-domains.squid
geo.settings-win.data.microsoft.com.akadns.net
db5-eap.settings-win.data.microsoft.com.akadns.net
settings-win.data.microsoft.com
db5.settings-win.data.microsoft.com.akadns.net
asimov-win.settings.data.microsoft.com.akadns.net
db5.vortex.data.microsoft.com.akadns.net
v10-win.vortex.data.microsoft.com.akadns.net
geo.vortex.data.microsoft.com.akadns.net
v10.vortex-win.data.microsoft.com
v10.events.data.microsoft.com
v20.events.data.microsoft.com
us.vortex-win.data.microsoft.com
eu.vortex-win.data.microsoft.com
vortex-win-sandbox.data.microsoft.com
alpha.telemetry.microsoft.com
oca.telemetry.microsoft.com
ceuswatcab01.blob.core.windows.net
ceuswatcab02.blob.core.windows.net
eaus2watcab01.blob.core.windows.net
eaus2watcab02.blob.core.windows.net
weus2watcab01.blob.core.windows.net
weus2watcab02.blob.core.windows.net
Next add the following into your squid configuration file /etc/squid/squid.conf:
acl telemetry dstdomain “/etc/squid/telemetry-domains.squid”
Final step, is to enable the deny rule to the acl (again in the main squid config file) /etc/squid/squid.conf :
http_access deny telemetry
Conclusion
Today we have translated and covered two options of blocking Microsofts telemetrics, where Defender may upload a confidential file to Microsoft servers, for the purposes of malware research. There are many other ways involving different proxies, DNS servers, and Firewalls. You can easily translate the German BSI document and discover the solution that best works for your organisation. So happy reading!
Share on: