Windows: NTFS Alternative Data Streams

TLDR;
Within your SIEM or 3rd-Party security scanning product you get alerted to an Alternative-Data-Stream (or ADS), and you see one or move of the following hidden streams.
- ♣3or4kl4x13tuuug3Byamue2s4b
- 3or4kl4x13tuuug3Byamue2s4b
- x05or4kl4x13tuuug3Byamue2s4b
- 4c8cc155-6c1e-11d1-8e41-00c04fb9386d
Note: x05 is the hex representation for the black club symbol
You might initially panic! That you may have been attacked or hacked? But actually this signature appears to be an undocumented feature of the Windows Fax and Scan service. The Windows Fax and Scan service actually appends these ADS files to any document or image scanned by the inbuilt Microsoft Windows Scanning software.
NTFS & Alternative Data Streams
NTFS (New Technology File System) is a proprietary journaling file system developed by Microsoft, and is the default filesystem for all Windows Operating Systems.
But what are Alternative Data Streams?
What is an Alternate Data Stream (ADS)?
Alternate Data Stream (ADS) is the ability of an NTFS file system (the main file system format in Windows) to store different streams of data, in addition to the default stream which is normally used for a file. When this feature was created, its main purpose was to provide support to the macOS Hierarchical File System (HFS).
The NTFS file system contains files with attributes. The relevant attribute for our scope is the $DATA attribute, which is used to store the data streams of a file.
In the past, it was common to store a malicious payload within an ADS of a legitimate file. But today, many security solutions will detect and scan ADS. However, not all ADS are malicious and some are infact digital watermarks, and/or perform another security purpose.
For instance, since XP SP2 when a file is downloaded from the internet (i.e. by clicking on a link in Explorer.exe) to an NTFS volume an Alternate Data Stream (Zone.Identifier) is created along side the downloaded file (i.e. downloadedfile.exe:zone.identifier). The content of this file is used as a security by Windows XP as security data to determine the publisher/source of the file.
The values in the following table are typically assigned,
- URLZONE_USER_MIN = 1000
- URLZONE_INTRANET = 1
- URLZONE_TRUSTED = 2
- URLZONE_INTERNET = 3
- URLZONE_UNTRUSTED = 4
If you were to run your 3rd party security tool or any of the below examples, you will typically find that the Zone.Identifier ADS is applied to all files within your user’s home directory Downloads folder.
Enumerating Streams
The following is an example of enumerating the data streams of a file with PowerShell:
get-item -path '.\Welcome Scan.jpg' -stream *
PSPath : Microsoft.PowerShell.Core\FileSystem::C:\Users\user\Documents\Scanned Documents\Welcome Scan.jpg:♣3or4kl4x13tuuug3Byamue2s4b
PSParentPath : Microsoft.PowerShell.Core\FileSystem::C:\Users\user\Documents\Scanned Documents
PSChildName : Welcome Scan.jpg:♣3or4kl4x13tuuug3Byamue2s4b
PSDrive : C
PSProvider : Microsoft.PowerShell.Core\FileSystem
PSIsContainer : False
FileName : C:\Users\user\Documents\Scanned Documents\Welcome Scan.jpg
Stream : ♣3or4kl4x13tuuug3Byamue2s4b
Length : 180
PSPath : Microsoft.PowerShell.Core\FileSystem::C:\Users\user\Documents\Scanned Documents\Welcome Scan.jpg:{4c8cc155-6c1e-11d1-8e41-00c04fb9386d}
PSParentPath : Microsoft.PowerShell.Core\FileSystem::C:\Users\user\Documents\Scanned Documents
PSChildName : Welcome Scan.jpg:{4c8cc155-6c1e-11d1-8e41-00c04fb9386d}
PSDrive : C
PSProvider : Microsoft.PowerShell.Core\FileSystem
PSIsContainer : False
FileName : C:\Users\user\Documents\Scanned Documents\Welcome Scan.jpg
Stream : {4c8cc155-6c1e-11d1-8e41-00c04fb9386d}
Length : 0
You can also use dir /R, or SysInternal’s streams.exe to enumerate an ADS of a file / recursively on a directory.
streams '.\Welcome Scan.jpg'
streams v1.60 - Reveal NTFS alternate streams.
Copyright (C) 2005-2016 Mark Russinovich
Sysinternals - www.sysinternals.com
C:\Users\user\Documents\Scanned Documents\Welcome Scan.jpg:
:♣3or4kl4x13tuuug3Byamue2s4b:$DATA 180
:{4c8cc155-6c1e-11d1-8e41-00c04fb9386d}:$DATA 0
Another options is to run one of the Nirsoft tools: AlternativeStreamView, which can also easily extract the ADS data:
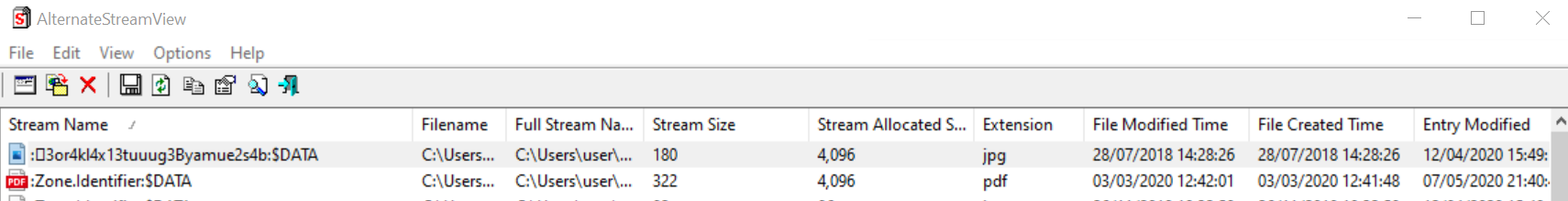
The extracted ADS data within a hex-editor looks like:
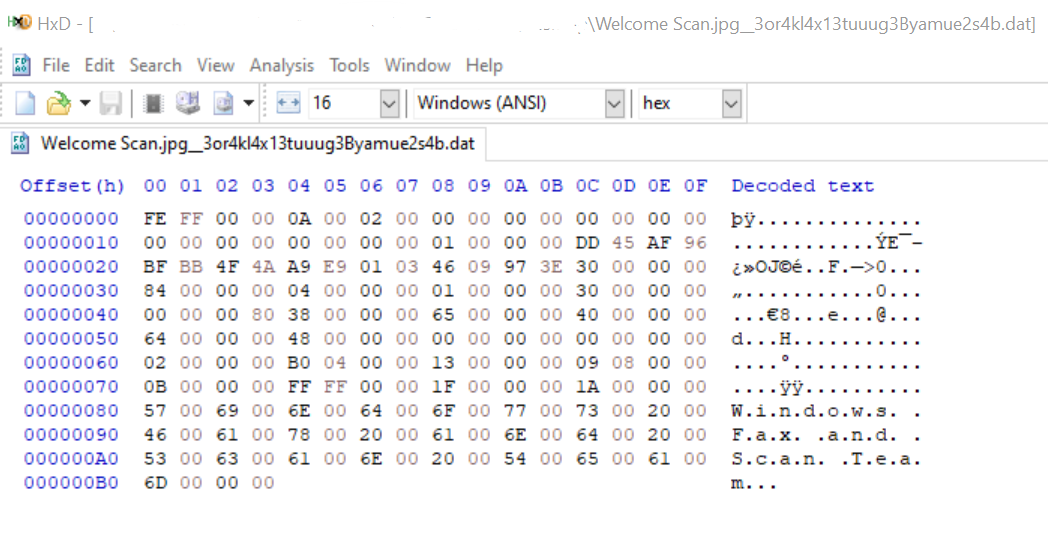
Conclusion
In the image above, you can clearly see that the data has been tagged by Microsoft Windows Fax and Scan Service. Having, checked on multiple systems, installs and variety of work and personal computers, we can find the same ADS signature on all Microsoft Windows Operating Systems. However, the size of the ADS does vary, we assume the file contains more data, such as possible timestamps and possible signatures of the scanning hardware, but we stopped investigating after figuring out this was actually a benign stream (NTFS ADS).
References
- https://www.dfir.training/artifacts/ads-zone-identifier-artifact
- https://docs.microsoft.com/en-us/sysinternals/downloads/streams
- https://www.nirsoft.net/utils/alternate_data_streams.html
Share on: