WhatsApp Phishing

TLDR;
With the recent spate of WhatsApp Phishing alerts in the media. Netscylla has had numerous requests from clients to conduct Incident Response on victim devices and break down the variations of attacks in a manner the stakeholders can understand, so that a decision could be made whether to continue using WhatsApp, or implement policies to govern its useage within a given business or department.
This blog post, discribed two different types of attacks we have witnessed in the past two months.
Method 1 – QR Code
This is the considerably the worst attack, as it actually syncs content with your phone – all contacts/media/photos/message history etc.
Actor will visit https://web.whatsapp.com/, and tick the box ‘keep me signed in’ to retain access.
Example QRcode from web.whatsapp:

They then screenshot the QR (like above) and send that via WhatsApp/Email/SMS, inviting you to join a group chat.
If the victim scans this code with their phone, they are actually pairing their WhatsApp phone data with the WhatsApp Web-Session. With full access to their history and content.
An actor can also request an account activity file – this takes 3 days to prepare. It contains a list of contacts and group names, their IP and phone info, and a profile picture if they set one up. Uninstalling and re-installing WhatsApp or changing phone number should stop this process.
Method 2 - SMS and/or WhatsApp Message
When an actor installs a fresh version of WhatsApp they can enter an email or phone number. WhatsApp will then send an SMS to the phone number to authenticate the user.
What the sneaky actor does is: try to claim you were sent that code by mistake, and that they need it urgently (they are normally masquerading as an already compromised colleague)!
Usually, what makes this attack successful is the un-modified group privacy settings.
Quick Note: Group Privacy Settings
By default WhatsApp sets your Group Provacy Settings to anyone! This means that anyone on WhatsApp can add you to their group chat.
We recommend changing this setting to: “My Contacts”
We advise following the instructions on this page to alter this setting:
Example of Attack
You may recieve the following in a newly formed chat group, or a spoofed or compromised friend/colleague in your contact list.
Example Message:
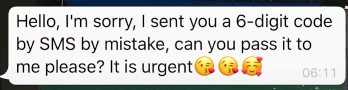
An example SMS received to your phone:
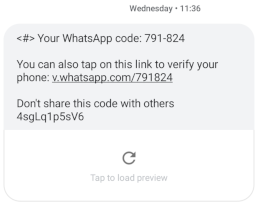
If you were to send them the genuine WhatsApp Code, they will gain access to your account. Where they have access to the following:
- Contact phone numbers
- Groups/Group names (with associated contact numbers)
All past chat history is blank, no past messages or access to media.
An actor can also request an account activity file – this takes 3 days to prepare. It contains a list of contacts and group names, their IP and phone info, and a profile picture if they set one up. Uninstalling and re-installing What’s App or changing phone number should stop this process.
Recommendations for People Caught out
- Backup WhatsApp data.
- Consider applying for a new mobile SIM and/or Phone number
- Uninstall & Reinstall WhatsApp (this should generate new crypto keys)
- Once logged in to WhatsApp - Setup 2FA
- While hardening your settings, don’t forget to adjust your Group Privacy Settings
- Notify all contacts you have been hacked, and to ignore/confirm any recent messages
Disclaimer
WhatsApp Logo is owned and trademarked by WhatsApp. Owned by Facebook Inc.
Share on: