Rapid Radio Device Reversing

Introduction
Netscylla caused an up-roar yesterday evening with many jealous stateside people, as we leaked the already public documentation for the latest Hak5 Pineapple - the fabled VII (Mk 7), which has been rumoured about, with data publically available since March 2020.
Apparantly, this was supose to be a secret? As their launch is today
- Do we own a Pineapple or other Wireless attack type of device: YES
- Can we make our own Wireless attack devices: YES
- Do we want to sell our own Wireless attack devices: NO
- Do we void warranties: AT OUR OWN RISK OR IN AGREEMENT WITH A CONTRACT/CUSTOMER
We will leave the questions there and start to highlight some of the wonderful work that has already been performed and is effortless to obtain.
SPOILER: Some may think we are revealing industry secrets - but we are not!
Reversing Radios
TLDR;
This has already been covered by Michael Ossmann, Michael has in the past performed a brilliant and informative talk(s) at Defcon and other conferences, and really these slides do not do him justice:
Picking a device
Alfa is a know provider for wireless equipment, we have over the past years owned several of their devices and have used them for connecting to wireless (802.11a/b/g/n/ac) networks. The best thing is that Alfa devices are resonably affordable and do not break the bank, and hardware should anything bad happen is trivial to replace.
TLDR; Getting the firmware
Alfa are very open about their support of and publish software and drivers for various Operating Systems, and as such we have the following links:
- Main Alfa website
- Download links for Drivers and firmware Also depending on your specific dongle, where appropriate there are WPA3 drivers available!
Getting the Device Specification
As Michael Ossmann highlighted we can use either of the following resources to uncover more information about radio based devices:
Now to begin searching you can enter the code from the bottom of the device (or possibly existing device), or search on company name
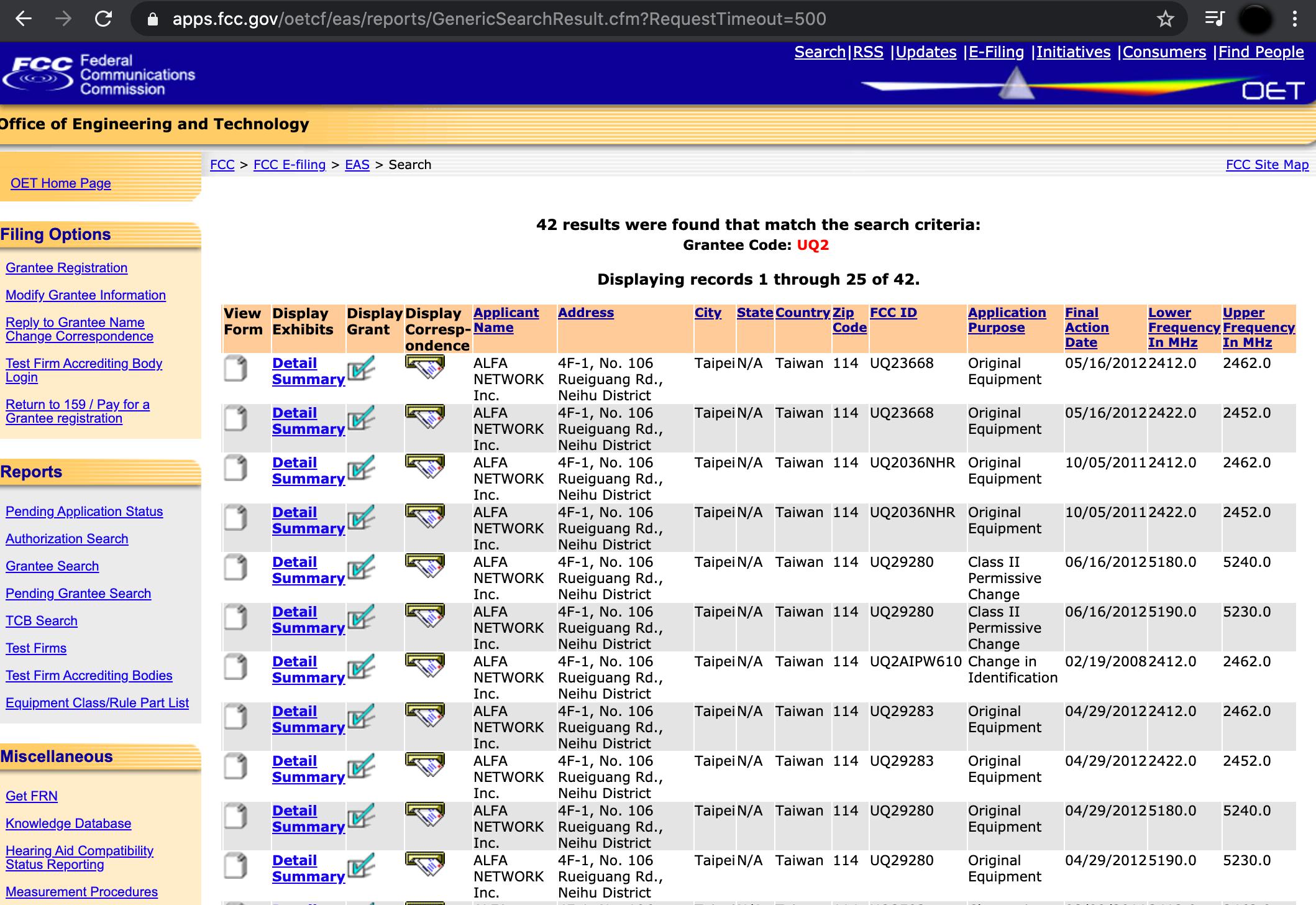
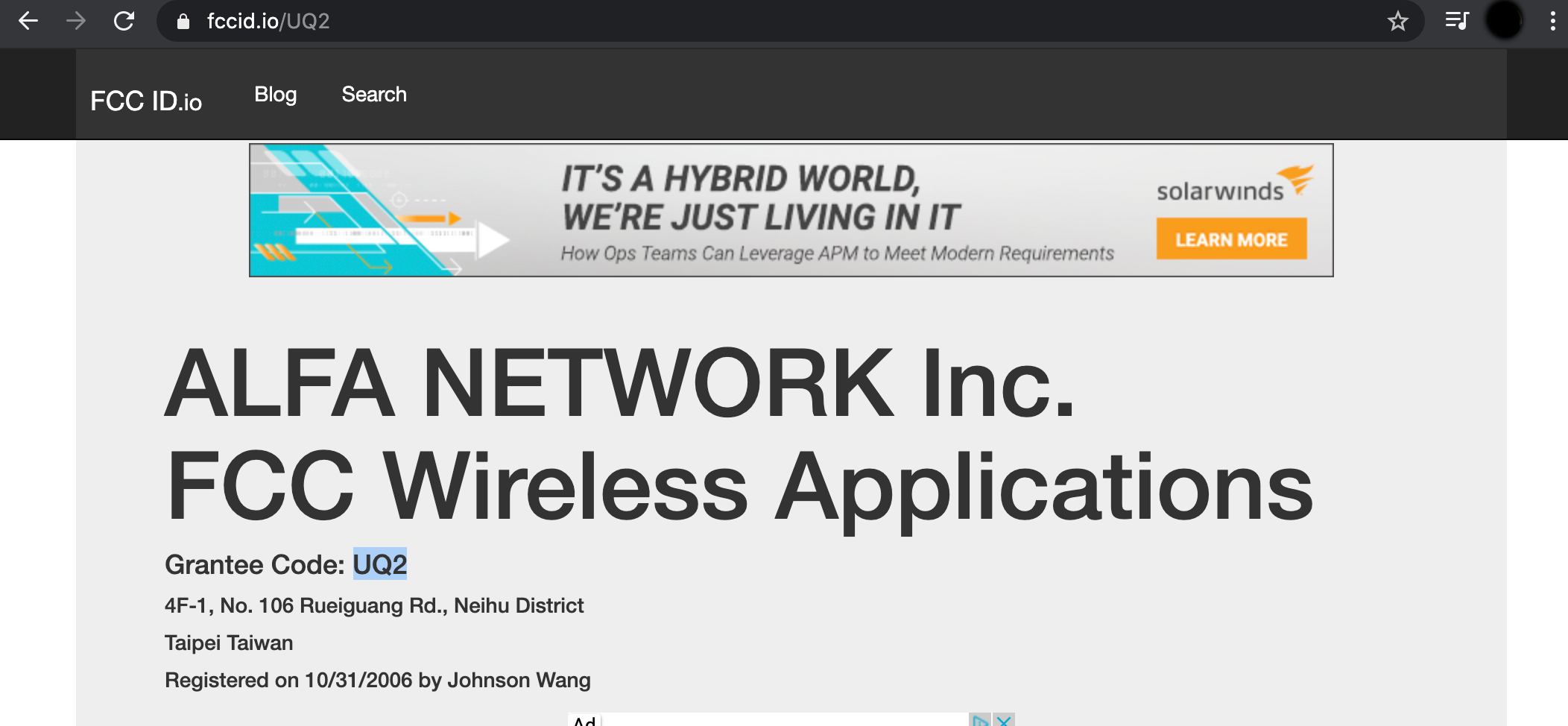
As you can see from the images above we can ascertain details about individual specific radio devices.
Picking a device at Random
The next few steps are based on visiting the following URL:
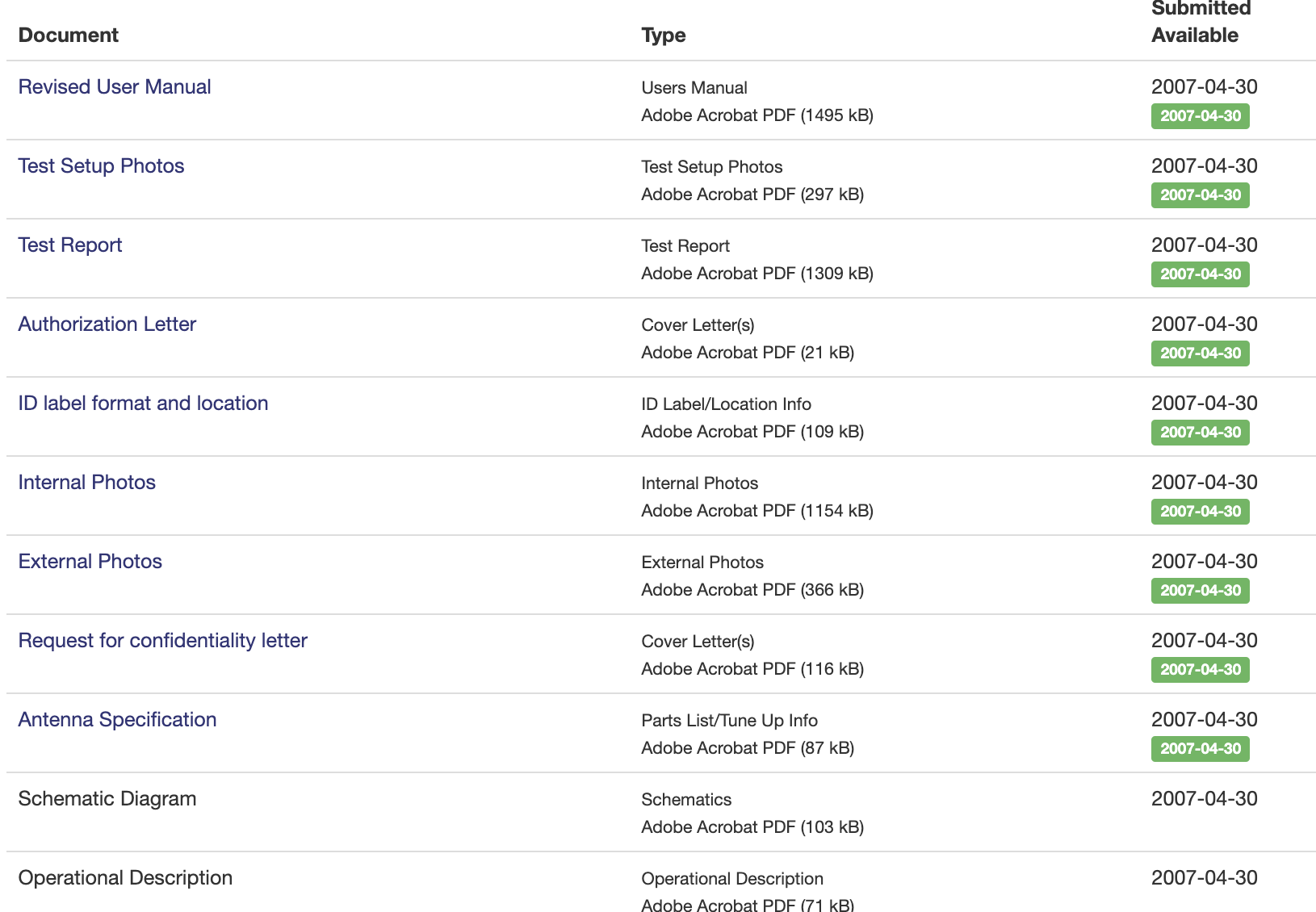
Whoa! A treasure trove of documentation:
- images
- testing results
- contract
- user manuals
- antenna specification
- schematics
This looks like the jackpot, we get a lot of information here, also a good read on the understanding of having certain docs classified as confidential is:
- Letter of Confidentiality
Usually this means the above data is usually kept as confidential until the Grant of Application is granted. Many firms time this perfectly with their manufacturing, marketing, and sales departments. Delays can be costly, but inefficiencies in a business that mean manufacturing or sales are not ready for whatever reason? Competitors can freely observe this information and start a fight in the market place.
For reverse engineers, this info is a goldmine, and is very helpful into understanding a radio device and its components. We can continue from this stage into the following steps:
- Search chip manufacturers, for data sheets on ICs, SOCs, Processors, Memory Chips
- Search company websites to download firmware and drivers
- Search Open-source communities for firmware and drivers
- Search research blogs, where other researchers have already queried the target device.
FCC Process
The steps for FCC authorisation may be hard to understand at first but the FCC have published this useful webpage https://www.fcc.gov/engineering-technology/laboratory-division/general/equipment-authorization. It has a nice step-by-step guide with links to extra reference material, to guide you through the entire process.
Why
But people still ask: Why perform OSINT on hardware?
We have quickly thought of the following reasons:
- Competition
- Reversing & Debugging
- Reversing - without voiding a warranty! :)
The last one can by quite useful, as it means not initially potentially destroying a device, and proving to a customer the information that is publically available. Could be used for research purposes to derive attack strategies and methodologies against a hardware device.
Conclusion
Understanding the FCC process, getting your business in tune with the correct stages, and being ready for market is crucial. Otherwise, any mistake and you may be giving your competitors an early start against competing aginst your product or business.
A little bit of hardware OSINT and you can possibly uncover so-called product secrets!
Getting a jump on a new product, and whether reviewing or revealing specifications (as additional documentation has to be filed if deviating from the original FCC Grant), could potenitally be a business winner. We achieved a new target audience of over extra 2000 individual page reads! The race to revealing details or reviewing a new product in a target market can be good for business.
There is always the possibility of more nefarious characters employing phishing, malware or even crypto-coin mining endpoints on a targetted landing page. So beware on what you click!
Disclaimer
Images and specifications were sourced using OSINT, FCC, FCCID. Most of the methodology was sourced from the awesome eye-opening work of Michael Ossmann.
Share on: