FIRST SecLounge CTF - Musee

Introduction
Below is our write-up of the 2020 Security Lounge CTF:
FIRST Seclounge CTF 2020 Challenge Walkthrough
It was a fun and interesting challenge, over a number of different topics. We made new connections with different Teams scattererd across the globe and made friends. It was a very enjoyable experience by all, and we look forward to re-connecting with our new firends in future challenges.
Musee Solution

If you have read our solution walkthrough, you will have reliased we ran out of time during the CTF and failed to complete thre Musee challenge in the alloted time. This blog post serves as the walkthrough for that challenge.
With Musee we are given an image. Straight away this has to be Steganography
Steganography
Steganography (/ˌstɛɡəˈnɒɡrəfi/ (About this soundlisten) STEG-ə-NOG-rə-fee) is the practice of concealing a file, message, image, or video within another file, message, image, or video. The word steganography comes from Greek steganographia, which combines the words steganós (στεγανός), meaning “covered or concealed”, and -graphia (γραφή) meaning “writing”. –Wikipedia
Stegdetect
Stegdetect is an automated tool for detecting steganographic content in images. It is pre-programmed with signatures of several steganographic tools, and can help incident responders and/or researchers to pin-point the specific algorithm or software that was used to create the secret message hidden within the picture.
root@4aa42d54d58b:/data# stegdetect musee.jpg
musee.jpg : f5(***)
From this output we can see that Stegdetect has found a signature for the F5 steganogrphy project.
F5 - First Attempt
We attempt to use F5 to extract a hidden message and possible flag.
$ git clone https://github.com/matthewgao/F5-steganography
Cloning into 'F5-steganography'...
remote: Enumerating objects: 64, done.
remote: Total 64 (delta 0), reused 0 (delta 0), pack-reused 64
Unpacking objects: 100% (64/64), done.
sansforensics@siftworkstation: ~
$ cd F5-steganography/
sansforensics@siftworkstation: ~/F5-steganography
$ java Extract
java Extract [Options] "image.jpg"
Options:
-p password (default: abc123)
-e extractedFileName (default: output.txt)
Author: Andreas Westfeld, westfeld@inf.tu-dresden.de
extract:
$ java Extract ../Downloads/musee.jpg
Huffman decoding starts
Permutation starts
4944384 indices shuffled
Extraction starts
Length of embedded file: 804127 bytes
(1, 536870911, -3) code used
Incomplete file: only 0 of 804127 bytes extracted
Unfortunatley, this hasnt worked! It’s likely that we also need a password?
Stego Veritas
We can use the Stegoveritas tool (self proclaimed ‘yet another stego tool’), to perfrom a number of different operations on the image. Hopefully, dumping several different masks of images and exif data should reveal some clues to the password?
We have a gpsposition
cat gpsposition
45 deg 30' 3.63" N, 73 deg 33' 20.91"
and a comment
# cat comment
JPEG Encoder Copyright 1998, James R. Weeks and BioElectroMech.
The comment has something strange… The name James R. Weeks and BioElectroMech are strings found in the sourcecode of the F5 stego tool, confirming what we detected with stegdetect.
The gps position refers to a house in Montreal Canada?
Google Image search
We use the Google Image search functionality on our stego image to figure out that the building is infact
- Centre d’histoire Montreal
- Google Street View
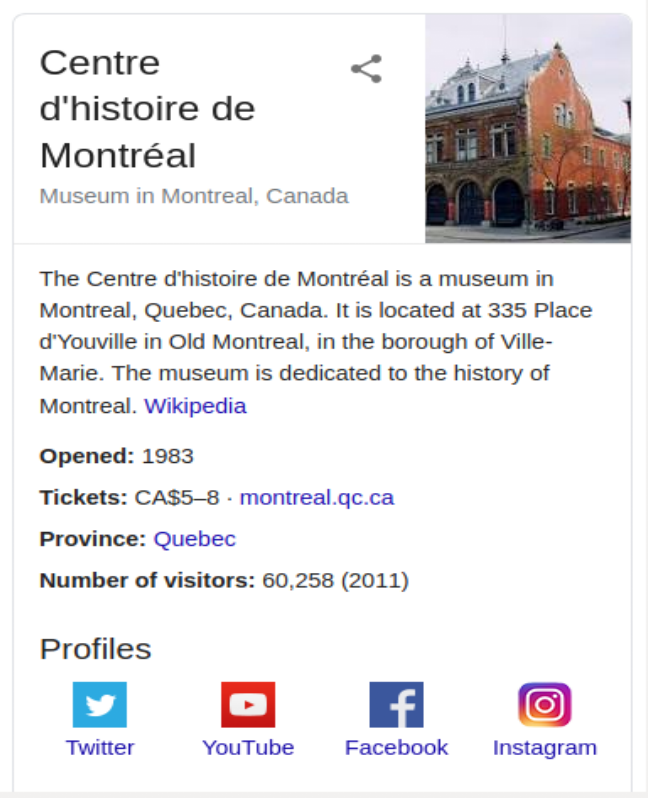

Looking at the building from street view, we can see numbers at the top of the image, that were not present on the doctored stego image? Could these digits be themagic password?
F5 - Second Attempt
Trying the password of 1903 was again unsuccessful!
F5 - Third Attempt
The creator of the challenge gave an extra hint that the password was x1903y - that we were missing 2 extra digits. After a few brute force guesses we find the password is : 219036
$ java Extract -p 219036 ../Downloads/musee.jpg
Huffman decoding starts
Permutation starts
4944384 indices shuffled
Extraction starts
Length of embedded file: 70 bytes
(1, 127, 7) code used
$ cat output.txt
Congratulations!
You found the flag!
322b91751fca3b9bb72eb410c7da1d1d
Share on: