Buspirate & UART to Debug Firmware
Introduction
We loaned our corporate Pineapple MK5 to one of our junior pentesters, for educational purposes only and for the safety of learning WiFi attacks in a controlled environment.
Unfortunately after many days of testing the Pineapple it suddenly stopped working? This was unexpected so we decided to look into how the Pineapple was booting; running the embedded OpenWRT Operating System to diagnose any possible software faults. Usually, this is typical of kernel modules installed on the sdcard that have become corrupt, or typically a corrupt sdcard? However, in this instance the sdcard yeilded no errors, and the sdcard EXT4 filesystem was intact.
Buspirate and UART
Fortunately, the Pineapple has a debugging UART interface, you could use a USB FTDI 3.3v to interface with the Pineapples console. But we prefer the multi-tool known as the Bus Pirate from dangerous-protoypes. According to dangerous-prototypes the Bus pirate is:
An open source hacker multi-tool that talks to electronic stuff.
It’s got a bunch of features an intrepid hacker might need to prototype their next project.
The Bus Pirate is availble from Seeedstudio
Or equally your local hobbyist electronics store.
Interfacing with the Bus Pirate
WARNING There are two varients of the Bus Pirate cabling, check which one you have here http://dangerousprototypes.com/docs/Common_Bus_Pirate_cable_pinouts, for this blogs purposes we are using the SeeedStudio varient.
The pinapple Mk5 has an exposed UART port on the back of the device. With the LEDs orientated on top, the pin out is as follows:
GND,RX,TX,3.3v
Using the Seeedstudio Bus Pirate we wire up the BP as follows (without connecting the v3.3):
Brown, Grey, Black, Nothing
Note: We dont wire up the 3.3v connector, now Hak5 issue a warning that connecting to this pin can brick the Pineapple. This probably needs further investigation, but we think the risk of bricking, is due to the interface lacking protection and the 5v from a typical USB based connection could be enough to blow chips that are only 3v tolerant.
Minicom
Our preferred console/serial interfacing software is minicom, which can be install on Linux (Debian) based systems as easy as
sudo apt install minicom
The minicom package should be available inside all package-managers, so use the one appropriate for your system.
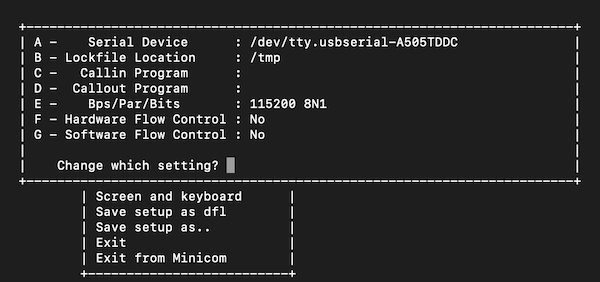
Next we need to establish our Bus-pirate’s /dev address. Ours has shown up as the following USB device, your’s may differ e.g. /dev/ttyUSB1
ls /dev/tty*
/dev/tty.usbserial-A505TDDC
We start minicom as follows, then use the cursor to navigate to modem setup.
sudo minicom -s
We then change the settings to reflect our device, and the speed and communciation settings of the Bus Pirate.
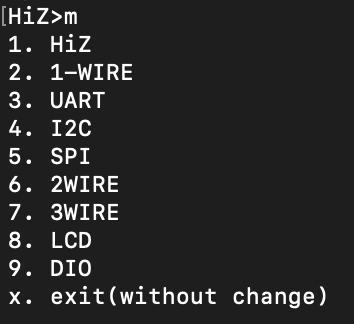
We enter macro mode via typing:
m
Then 3 for UART:
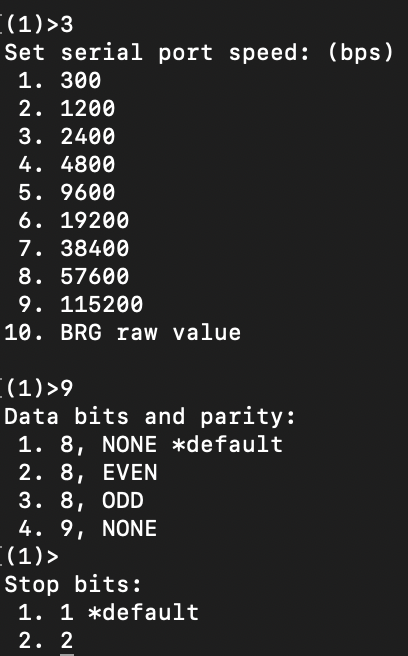
We run the macro by typing the following, and answering yes to the UART bridge question. As shown in the screenshot below:
(1)
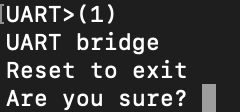
Upon rebooting the Pineapple we can see it boots as expected.
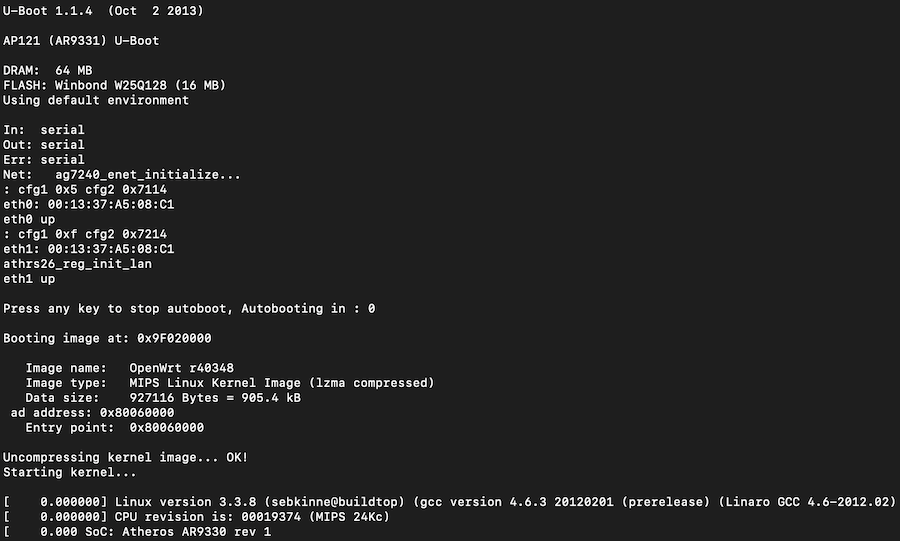
After booting we encounter a problem. The serial console constantly repeats SQUASHFS errors. It looks like our firmware has become corrupt? as we suspected.
[ 288.909481] SQUASHFS error: squashfs_read_data failed to read block 0x11b3773e
[ 288.909490] SQUASHFS error: Unable to read data cache entry [11b3773e]
[ 288.909494] SQUASHFS error: Unable to read page, block 11b3773e, size 17512
[ 288.909531] SQUASHFS error: Unable to read data cache entry [11b3773e]
[ 288.909534] SQUASHFS error: Unable to read page, block 11b3773e, size 17512
[ 288.909557] SQUASHFS error: Unable to read data cache entry [11b3773e]
[ 288.909561] SQUASHFS error: Unable to read page, block 11b3773e, size 17512
Delving deeper into the problem
Fortunately the Pineapple has a rescue mode, so we switch the DIP switches on the side of the MK5 into the following combination.
up,up,up,up,down
We manually reboot the device by removing, and re-connecting the power, and wait for the Pineapple to boot into u-boot mode.
Next we run mtest to check the condition of the memory chips. WARNING this will take a long time.
uboot> mtest
Testing RAM 0x802000000 to 0x838000000
You may not want to run the memory test command as it takes a long time. You may just want to skip to the next section on reflashing the base Pineapple image.
We left our memory test run for a day - the test completed with no errors, so therefore the memory is fine, and we can only think that somehow the SQUASHFS filesystem has become corrupt?
Reflashing the Pineapple
Connect an ethernet cable between your computer and Pineapple and then manually reboot the Pineapple. The pineapple should boot into rescue mode, and then you can reinstall the firmware by navigating to the webpage on http://192.168.1.1. Though you will have to set a static address on your computers ethernet interface first.
We upload the base firmware mk5_factory.bin, and follow the insstructions: such as reset the DIP switches to:
up,up,up,up,up
Reboot the Pineapple, and follow the normal update process, to upgrade to the latest MK5 version of 2.4.0
Conclusion
The Bus Pirate is an interesting hardware hackers tool. Not only is it the swiss-army knife of hardware for talking to different chips, and different chip protocols. We can use it to help debug software issues in firmware, establish console sessions and potenital shell access on unsecured hardware, and potenitally recover secrets that can unlock other areas of the firmware that were previously unknown or restricted.
Share on: