Pentest Reporting & Information Leaks

Information Leaks & Potential Confidential Data.
Security professionals now and again like to show off with public pentest reports. Or as part on the attempt to win new and additional work they will anonymise a report so show their likely understanding of the customers environment, and demonstrate how they test for vulnerabilities and provide remediation advice.
However, these testers often make a big mistake! They dont redacted the information, making it possible to recover the original and potentially confidential information.
We will highlight some of these big mistakes below. These are examples from various pentest reports from the github repo:
Example 1 Blocked Hashes
From the screenshot below, you can see that the hashes are blocked out by red and blue boxes.

No problem, just use a PDF editor and delete the boxes to reveal the hashes.

Now we can use OCR software to extract the text and crack the hashes.
$ ~/JohnTheRipper/run/john --wordlist=rockyou.txt dump.txt
Loaded 22 password hashes with no different salts (LM [DES 128/128 AVX])
Warning: poor OpenMP scalability for this hash type, consider --fork=4
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
FREEDOM (1228:1)
PASSWOR (3509:1)
COWBOY7 (1242:1)
LUKEJAM (9946:1)
MONDAY2 (7596:1)
MONDAY0 (7432:1)
3 (1242:2)
2 (6294:2)
4 (7596:2)
8 (9843:2)
27 (9851:2)
SKIING5 (9843:1)
...
$ ~/JohnTheRipper/run/john --show dump.txt
3509:PASSWORD7:1626:E52CAC67419A9A227920C5D817A72D61:8FD992DD15CA326310CA8471DE1289DC.
9851:LOJONG127:1628:81374D19DB8E66C1025A32A63FE04BEC:667007C56CE4C598612C218941726E06.
6294:POPPY.52:1629:98799ADB78B58D641D71060D896B7A46:DCE78AFBF7D15DCAA2C120066413EC94:.
9843:SKIING58:1637:DDF80F3F2DBD5FAB36077A718CCDF409:86F9033BC09B652537E70C0070387965:.
7596:MONDAY24:1638:81867B7F883635B7FF17365FAF1FFE89:84A0E0A11600AE47A75AC50900BACD48.
9946:LUKEJAMES0:1642:E4833763F6C5A6E76A60E82180378F7B:C298C37CC4336AB974E30396BOCZEFAO.
1228:FREEDOM???????:1644:29420448F4289C3A81400584657A9C46:E08021E5A7349576076363AC5F1F8312
1242:COWBOY73:1652:DFA346DBFC999A981AA818381E4E281B:F3E606018018DE77F21C1F7BBE359660
And onwards to cracking the NT Hashes!
Note: The OCR parsing has been quick and dirty and not entirely accurate, but this is to demonstrate that we can actually recover passwords:
$ ~/JohnTheRipper/run/john --wordlist=rockyou.txt --format=NT --show dump.txt
7432:Monday01:1610:5A426EFF12388C40C2265823734E0D4C:C999F63D8DEE068F39A0BA4DF3BAABE1:
6294:poppy.52:1629:98799ADB78B58D641D71060D896B7A46:DCE78AFBF7D15DCAA2C120066413EC94:
...
Example 2 Blocked Admin Credentials
Again, another example of a potentially dangerous leak:
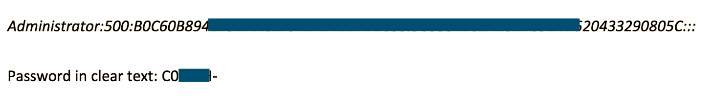
Delete the box and we can find the full hash and the admin credentials in plain-text
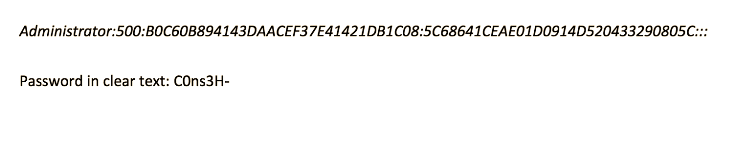
Example 3 Blocked Admin Credentials
Hmm, someone as obfuscated the ASCII data of the packet, but what happens when we delete the blue boxs
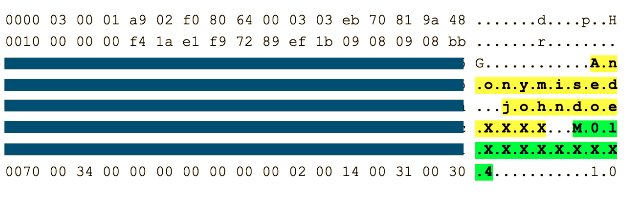
Aha, we can see data that does not relate to the ASCII, we can use the linux command line tool xxd to decode the hex
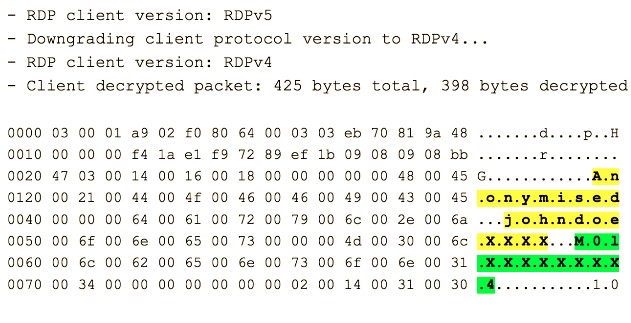
echo "48 45 21 44 4f 46 46 49 43 45 64 61 72 79 6c 2e 6a 6f 6e 65 73 4d 30" \
|xxd -p -r
HE!DOFFICEdaryl.jonesM0
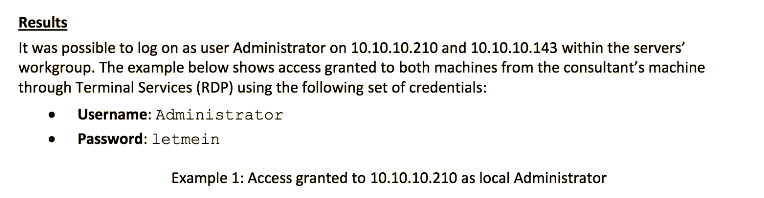
Example 4 Another example of leaked Admin Credentials
By now you should understand how to remove image blocks, that were previously masking confidential data
Remediation
- Pentest reporters should use proper and efficient data sanitisation tools.
- Images should be treated separately and content should be redacted in the original layer not adding layers, or applying floating image boxes.
- Simply masking the data using image boxes in Microsoft Word, Adobe, or 3rd party PDF products is insufficient.
- Do not forget about sanitising meta-data from images and documents.
- Pentesters should pentest their anonymised reports before publication
Share on: